
Enumeration
|
|
|
|
- Google search OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 exploit
- https://www.exploit-db.com/exploits/40136
|
|
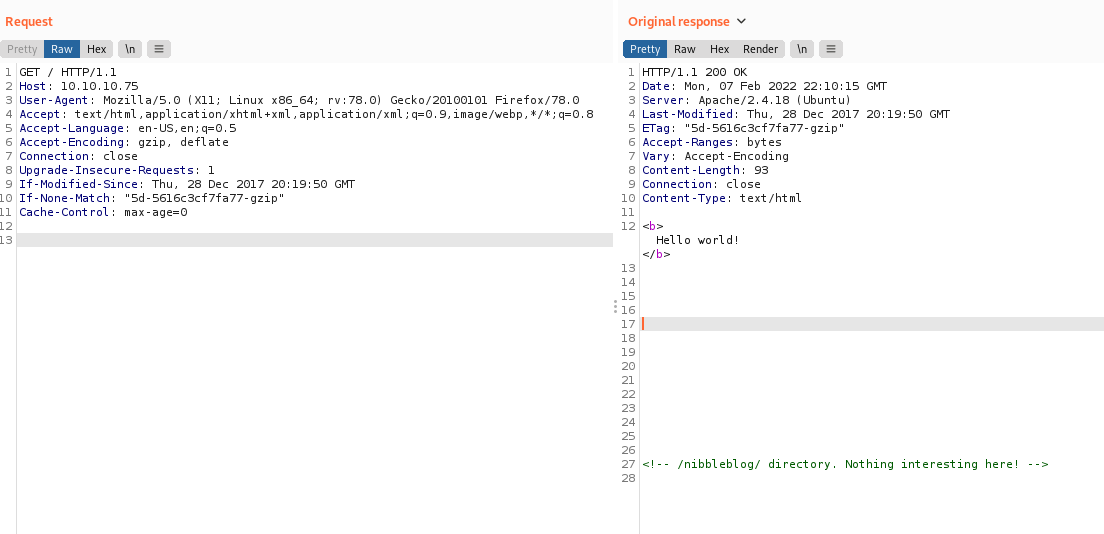
Burp the website http://10.10.10.75
|
|
- http://10.10.10.75/nibbleblog/
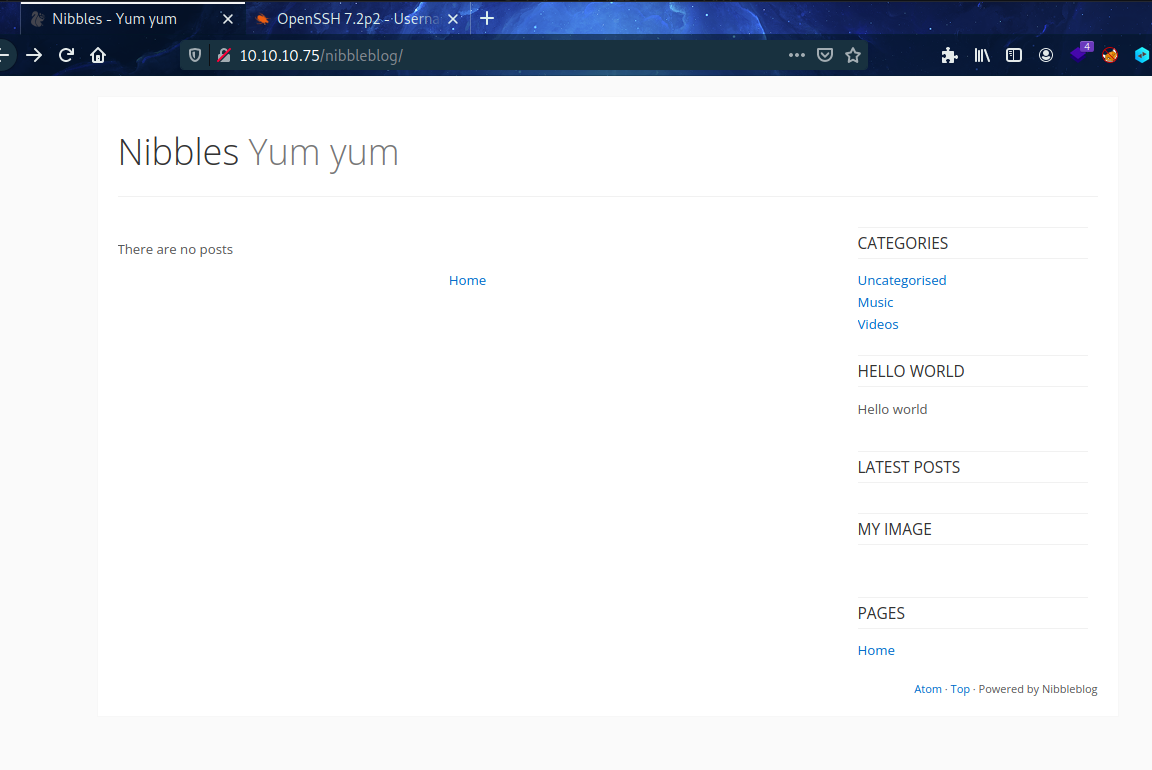
Directory Enumeration
|
|
|
|
|
|
|
|
- Going tohttp://10.10.10.75/nibbleblog/content/
- private → users.xml
- Found User: admin
Brute force with hydra
|
|
|
|
- No valid password for admin
- Login fort eh admin pagehttp://10.10.10.75/nibbleblog/admin.php
- username: admin | password: nibbles
- Nibbleblog info in →http://10.10.10.75/nibbleblog/README
- Version: v4.0.3
- Codename: Coffee
- Release date: 2014-04-01
- How to get reverse shell →https://packetstormsecurity.com/files/133425/NibbleBlog-4.0.3-Shell-Upload.html
Exploitation
|
|
- Upload the file via http://10.10.10.75/nibbleblog/admin.php → Plugins → My Image _> Configure → Browser → Save Changes
- Ignore the errors
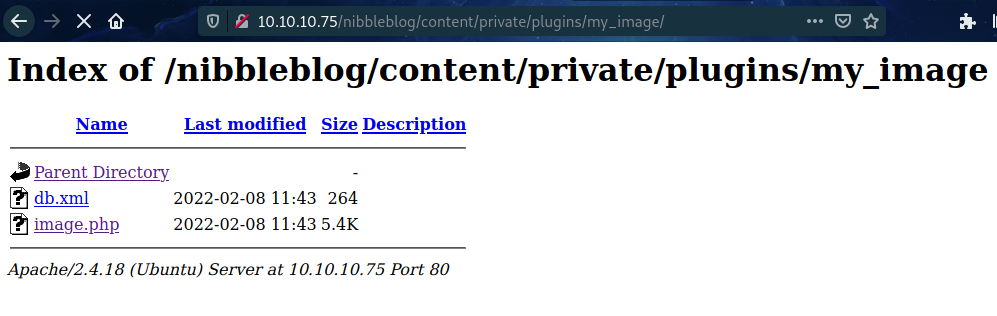
- To execute the file go to →http://10.10.10.75/nibbleblog/content/private/plugins/my_image/
|
|
Make shell interactive
|
|
Escalate Privileges
|
|
Exploit through metasploit
|
|
- admin : nibbles
|
|
|
|
Spawn shell
|
|
|
|
Skills Learned
- Enumerating web applications
- Guessing probable passwords
- Bypassing login rate limiting
- Exploiting NOPASSWD