Enumeration
|
|
|
|
Exploitation
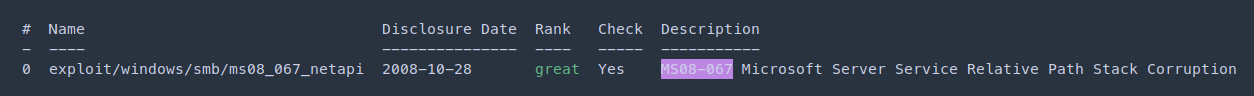
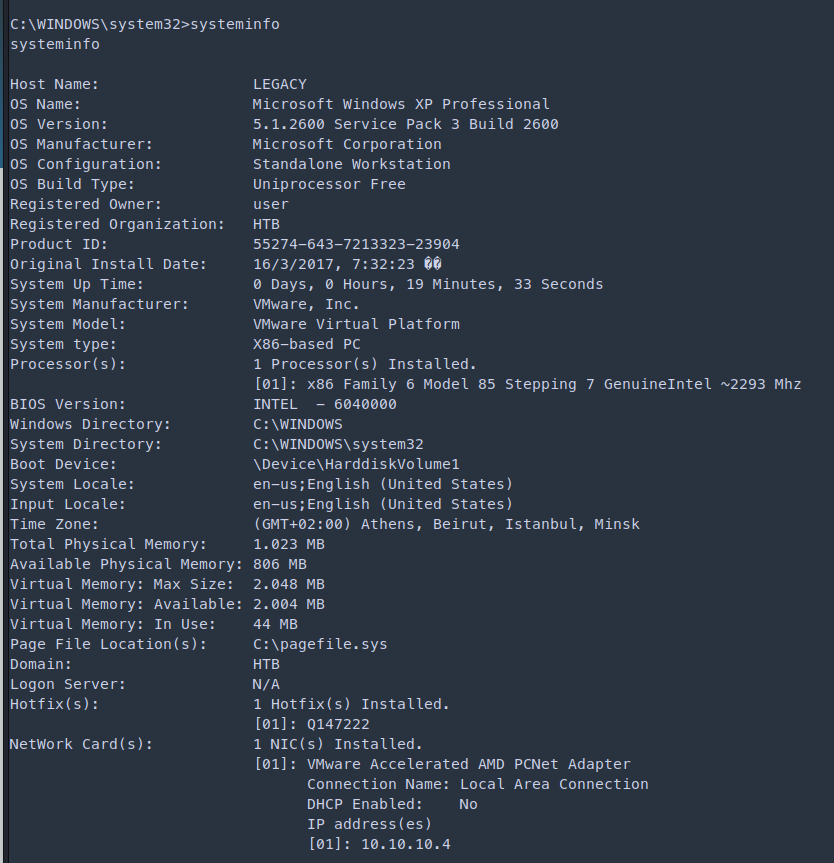
Came across that the application is vulnerable to MS08-067. https://www.rapid7.com/db/modules/exploit/windows/smb/ms08_067_netapi/
|
|
|
|
|
|
|
|
Skills Learned
- Identifying vulnerable services
- Exploiting SMB