Reconnaissance

|
|
|
|
Exploitation
- Going to → https://10.10.10.17/ and viewing the certificate information
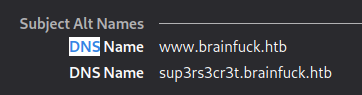
|
|
- Accessing both → https://brainfuck.htb/ and https://sup3rs3cr3t.brainfuck.htb/
Wordpress scan
|
|
|
|
- Found 2 users admin and administrator
- Plugin vulnerable → [+] wp-support-plus-responsive-ticket-system (Version: 7.1.3 (100% confidence))
|
|
|
|
|
|
- After creating the payload we can host the form using python
python -m SimpleHTTPServer # within the file that contains the html form
go to -> localhost.com:8000 and click login
go back to the website -> https://brainfuck.htb/ # We are logged-in
##SMTP
- Going to Dashboard → Appearance → Editor
- The files are not writable to get a shell
- Going to Settings → Easy WP SMTP
- Found:
- SMTP username: orestis
- SMTP Password: kHGuERB29DNiNE # Inspect element on the password field to get the password
- Found:
|
|
- Open the evolution program → next → next
Full Name: Orestis
Email Address: orestis@brainfuck.htb
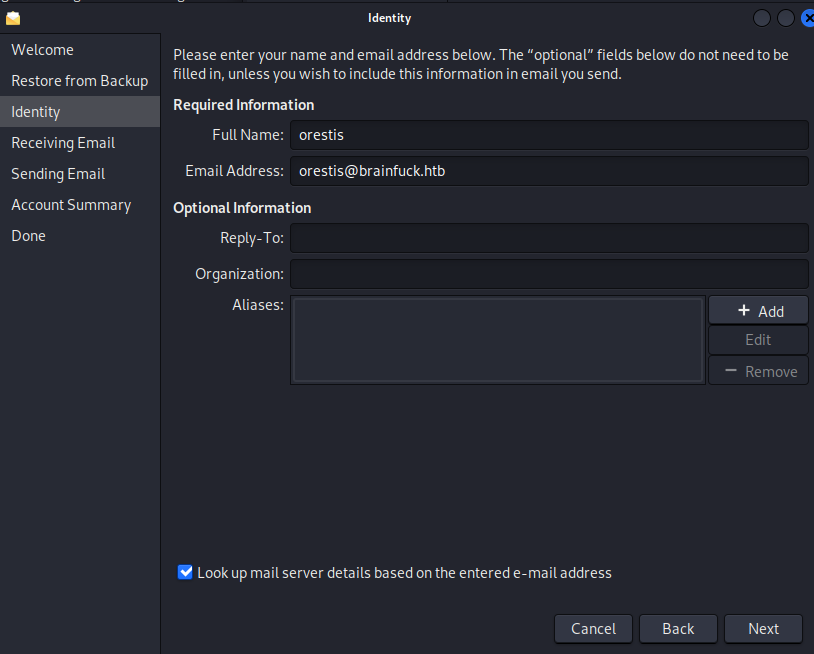
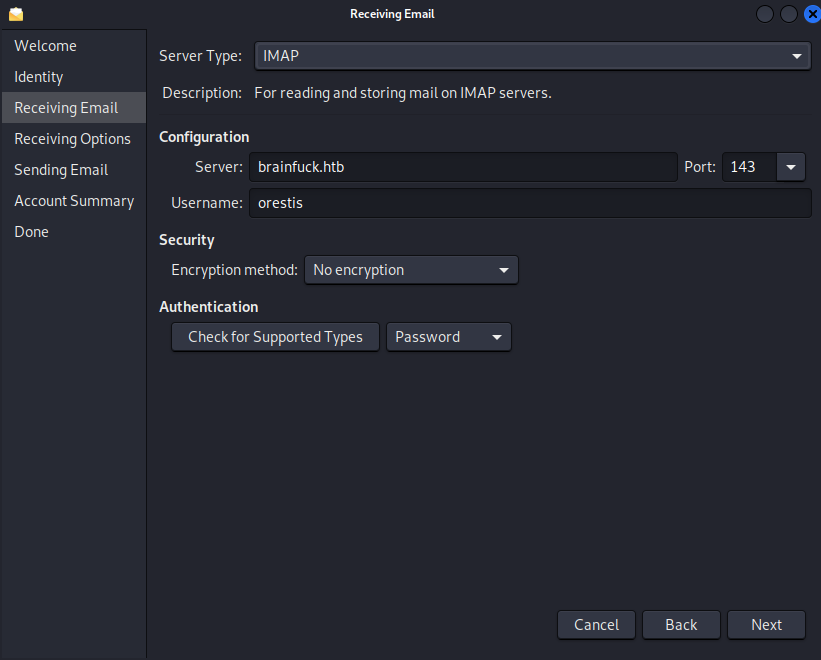
- Server: brainfuck.htb
- Username: orestis
- Port: 143
- No encryption
- Skip Options
- Server: brainfuck.htb
- Port: 25
- Encryption method: No encryption
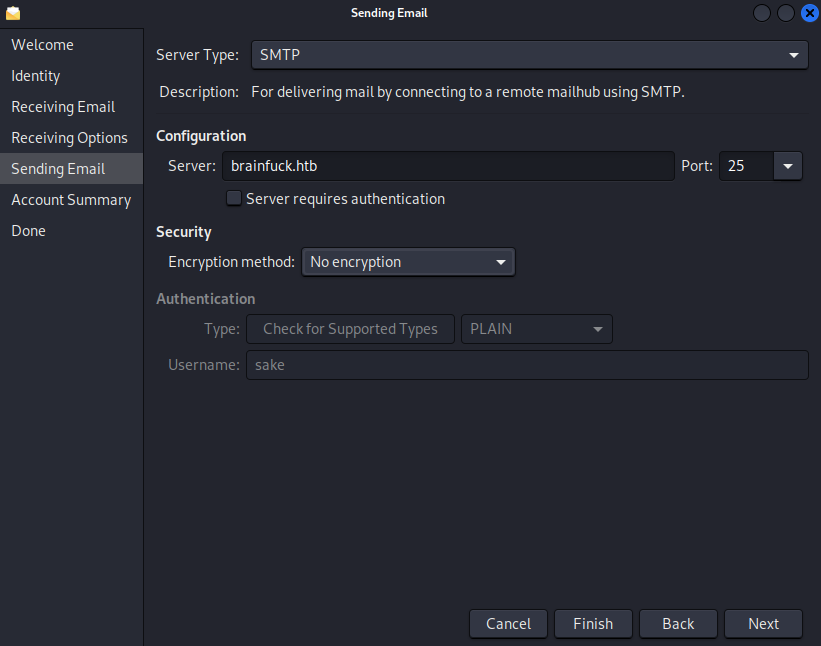
Enter the password in the mail application: kHGuERB29DNiNE
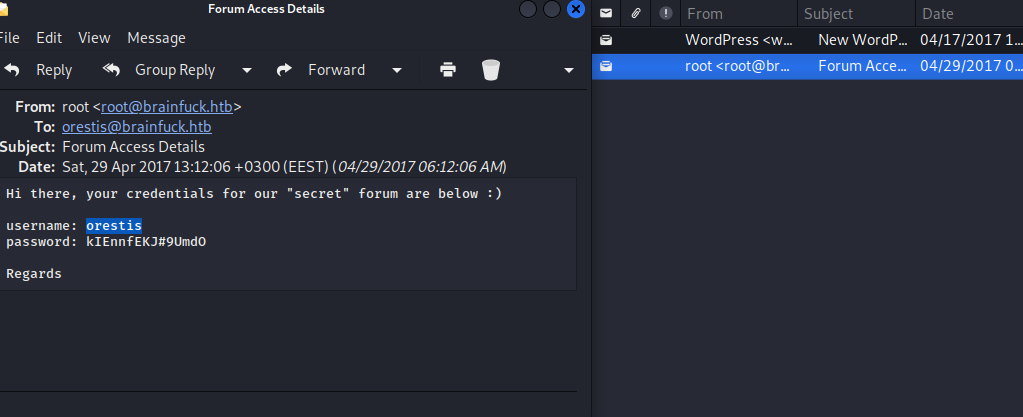
|
|
- Creds -> username: orestis | password: kIEnnfEKJ#9UmdO
|
|
- Login with the creds found in the Super Secret Forum
- orestis | kIEnnfEKJ#9UmdO
- Identified that is Vigenere cipher
- https://www.dcode.fr/vigenere-cipher
- Vigenere Ciphertext → Pieagnm - Jkoijeg nbw zwx mle grwsnn
- Keypassword → Orestis - Hacking for fun and profit → Brainfu - Ckmybra inf uck myb rainfu → brainfuck
- https://www.dcode.fr/vigenere-cipher
- Decipher the rest of the message
|
|
Interesting → There you go you stupid fuck, I hope you remember your key password because I dont https://10.10.10.17/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa No problem, I’ll brute force it Orestis - Hacking for fun and profit
- We have encrypted id_rsa we need to use JohnTheRipper. We will be using ssh2john.py
|
|
- Found ssh password 3poulakia!
|
|
Privilege Escalation
|
|
- Google and paste p = random_prime(2^floor(nbits/2)-1, lbound=2^floor(nbits/2-1), proof=False)
- →https://ctftime.org/writeup/6434. It is RSA
- Google how to decrypt RSA p q e
|
|
|
|
|
|
|
|
- Convert decimal to Hex →https://www.rapidtables.com/convert/number/decimal-to-hex.html
- Convert Hex to String →https://string-functions.com/hex-string.aspx
|
|
Skills Learned
- Enumerating SSL certificates
- Exploiting Wordpress
- Exploit modification
- Enumerating mail servers
- Decoding Vigenere ciphers
- SSH key brute forcing
- RSA decryption techniques